Paul Schwarzenberger
@paulschwarzen
Cloud Security Architect and DevSecOps
ID: 1045982795003297793
29-09-2018 10:25:06
170 Tweet
624 Followers
141 Following

Thanks jessica Glenn Wilson (DevSecOps) 🇺🇦 Steve Giguere Francesca 🙌 for inviting me to present “Road to IAM Zero” at DevSecOps London Gathering on Wednesday 25th October at Investigo - I look forward to seeing you there 😀 Sign up at meetup.com/devsecops-lond…


Looking forward to discussing #cloudsecurity at the C-Vision International CISO ThinkTank on Thursday 5 October 🚀

Good to see Sam Stepanyan as a candidate for the OWASP® Foundation 2023 Global Board of Directors election 🎉 Sam has done an amazing job for many years leading OWASP London, OWASP Project Nettacker, organising and speaking at OWASP conferences and events 🚀



Many thanks to Vandana Verma 🙏 for inviting me to speak about OWASP Domain Protect on your OWASP® Foundation Spotlight series 🙂 Sam Stepanyan appreciate you introducing us and making the suggestion 🚀 youtube.com/watch?v=KoP1X1…

Looking forward to presenting "Road to IAM Zero" at DevSecOps London Gathering on 25 October 🙂 5 steps to eliminate insecure IAM users from your Amazon Web Services org 🎉 world first public live demo of a new AWS Identity service feature 🚀 signup: meetup.com/devsecops-lond…



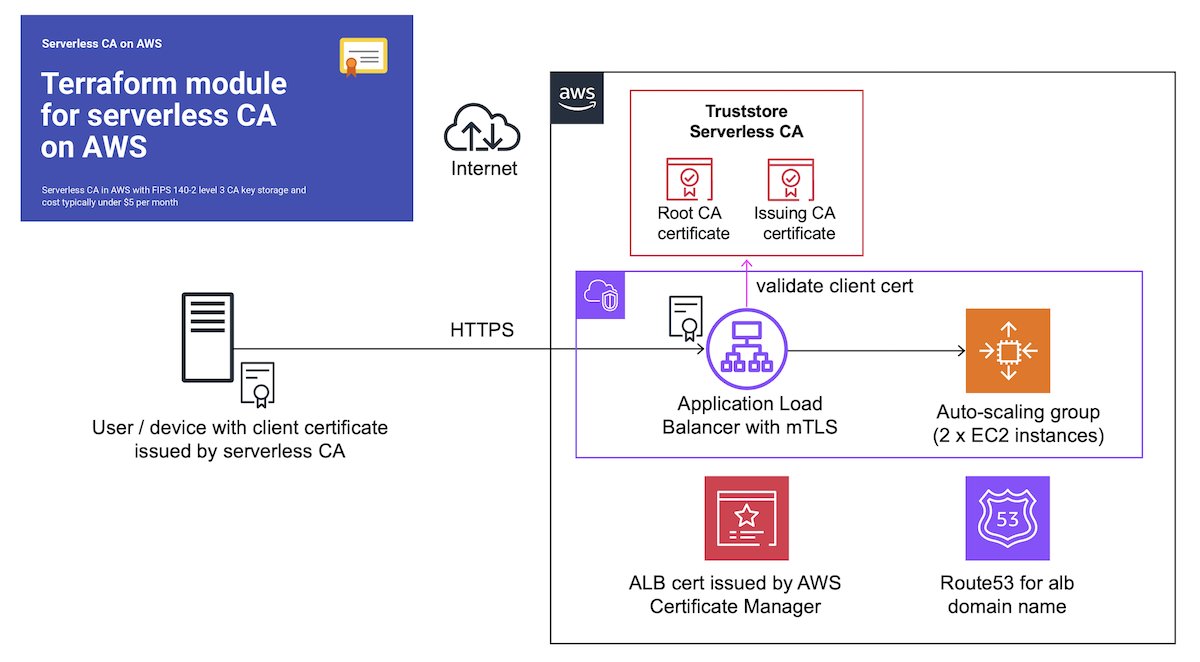
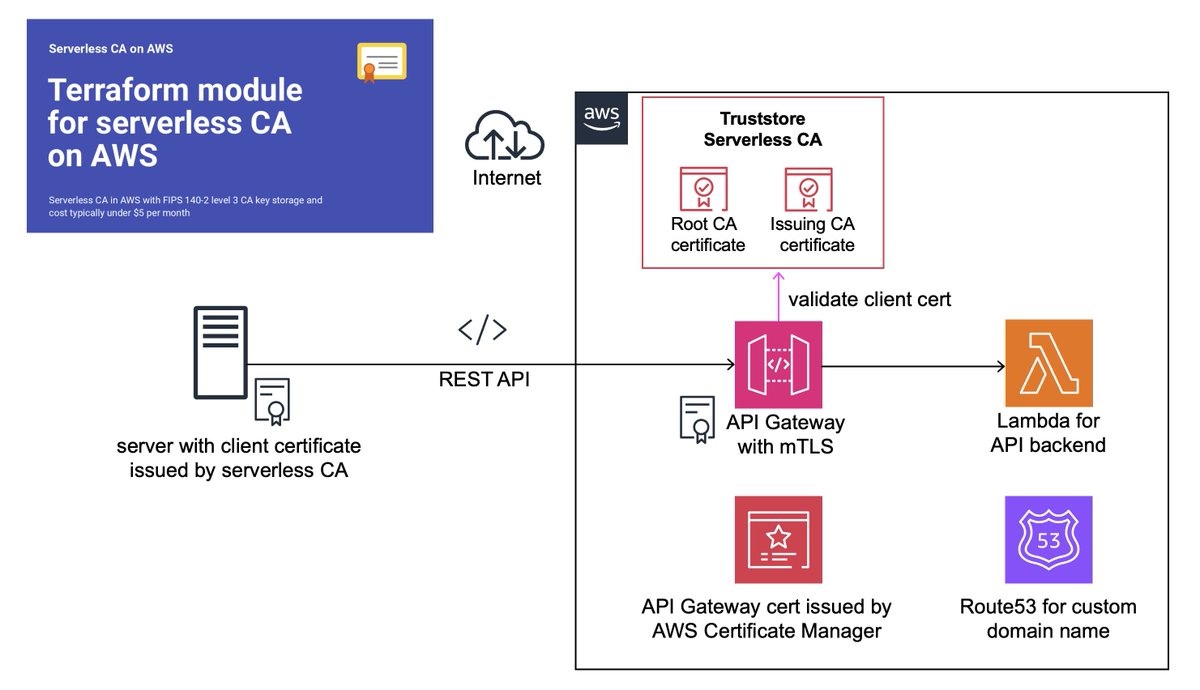
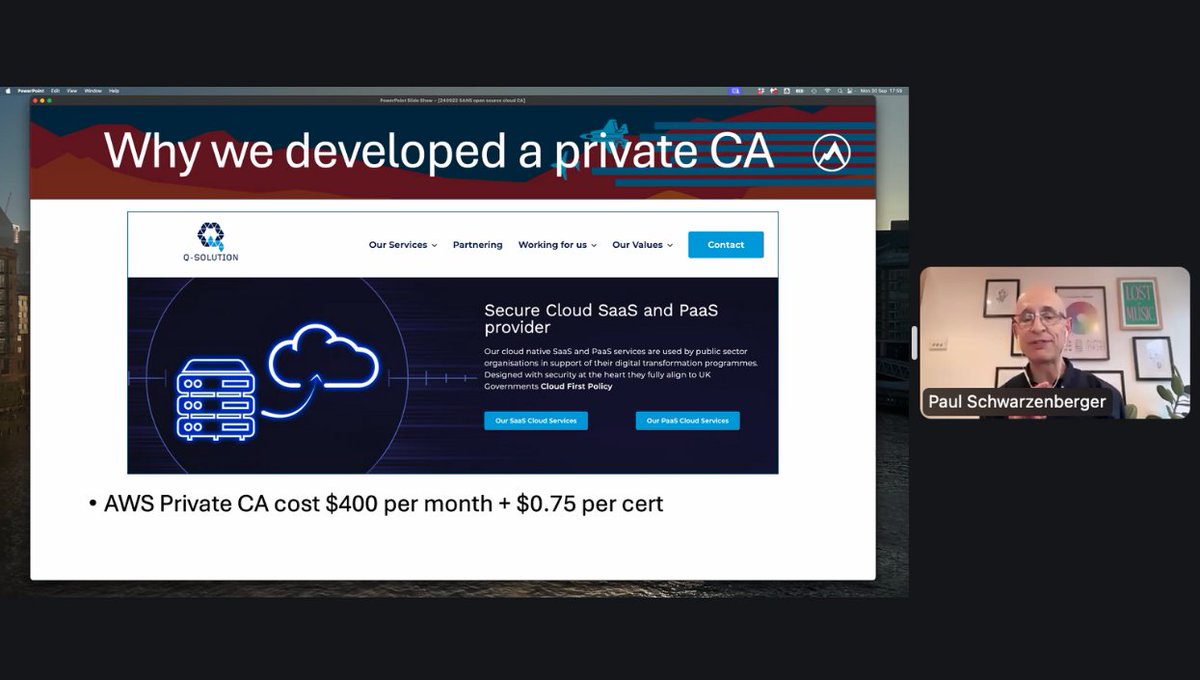
🚀New open-source cloud CA on #AWS costs $50 per year instead of $10,000 using AWS Private CA. Thanks Dhruv AHUJA for your review and contribution 🙂 Docs at serverlessca.com


Thanks Clint Gibler Corey Quinn Victor Grenu Marco Lancini for all featuring our new #opensource #Serverless certificate authority project 🚀 in your awesome security newsletters 🙌 serverlessca.com



🛎️ AWS Security Digest 164 is ready! 1️⃣ Rami McCarthy on exposed SSM documents 2️⃣ Paul Schwarzenberger with a AWS IAM Roles Anywhere tutorial 3️⃣ Palo Alto Networks exploring cloud VM attack paths awssecuritydigest.com/past-issues/aw…

Many thanks to CloudSecList AWS Security Digest Marco Lancini Jones Zachariah Noel ☁️ for featuring my blog post in your newsletters 🙂 medium.com/@paulschwarzen…


Join us at the SANS #CloudSecNextSummit where Paul Schwarzenberger will unveil an exciting open-source project! Stay tuned for an interactive, live demonstration of the CA and mTLS use case. Secure Your Spot and Register Today: sans.org/u/1uDe


First public live demo of our new #OpenSource private cloud CA later today at SANS Cloud Security #CloudSecNextSummit 🚀 sans.org/u/1uDe


Starting Now on Track 2 at #CloudSecNextSummit | Paul Schwarzenberger is discussing an open-source serverless #cloud Certificate Authority. Join us to learn how to implement a secure, cost-effective CA for your systems. ➡️ Register Free & Join: sans.org/u/1uDe #CloudSecurity

How a student on my cloud security training course ended up accessing underlying AWS infrastructure 😮 Thanks Aidan W Steele your post on CloudShell helped me understand what was going on 🚀link.medium.com/aTetDu8SINb



Recent talk at SANS Cloud Security on our #OpenSource #Serverless cloud certificate authority now on YouTube 🚀 youtu.be/JJD2GrZxLq4?li…


Catch up on this year's #CloudSecNextSummit talks featuring Frank Kim @emjohn20 Bailey Bercik - @[email protected] Jef Kazimer Kyler Middleton Paul Schwarzenberger Mandy Andress Brian Davis Mattias Borg and more! Playlist is now available ▶ youtube.com/watch?v=wIGevu…