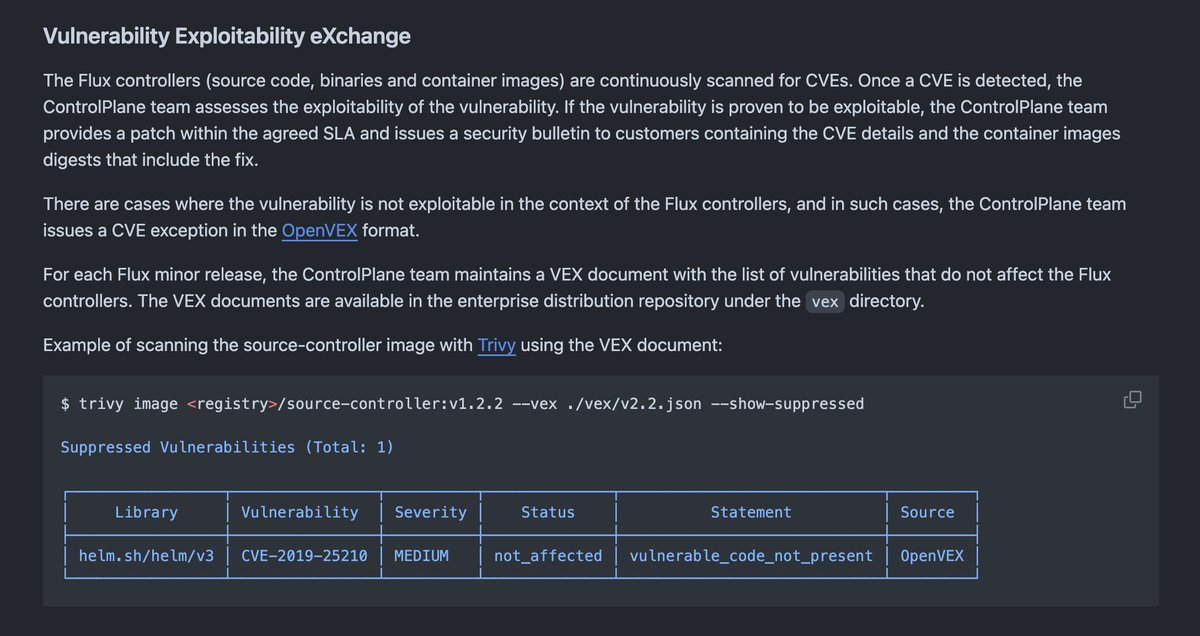
puerco
@puerco
Adolfo García Veytia / Technical Lead @Kubernetesio SIG Release / Staff Software Engineer @StackLokHQ / historian / WorldCyclist / fmr @chainguard_dev @uservers
ID: 3387071
https://hachyderm.io/@puerco 04-04-2007 03:04:19
7,7K Tweet
2,2K Followers
1,1K Following











Next Tuesday join me and Stacey Potter to kick off our new series of fun conversations about the software supply chain! For our first episode, we managed to convince Luke Hinds to be our test subject (sorry Luke!) Send your questions and don't forget to Bring Your Own Tacos!