
Luke Roberts
@rookuu_
Red Team. Ex-@mwrlabs Ex-@FSecure_Consult
Programmer | Hacker | MathComp Grad @ UCL
ID: 3832595577
http://themacpack.io 01-10-2015 10:28:33
272 Tweet
753 Followers
469 Following




Okay! We did it with Wojciech Reguła ! Another round of TCC vulnerabilities are coming! Next up at Blackhat Asia 🎉🎉 : “The Final Chapter: Unlimited ways to bypass your macOS privacy mechanisms” blackhat.com/asia-24/briefi…


We’re thrilled to share the news of our partnership with our friends Patrick Wardle & Mikhail Sosonkin over at DoubleYou! At Phorion our mission is simple: empower defenders with the tools they need to protect their macOS estates - no compromises. Partnering with the industry experts


This is huge for Phorion, having integrated the technology built by Patrick Wardle and Mikhail Sosonkin into our product, we’ve teamed up with the best minds in the industry. 🤜🤛


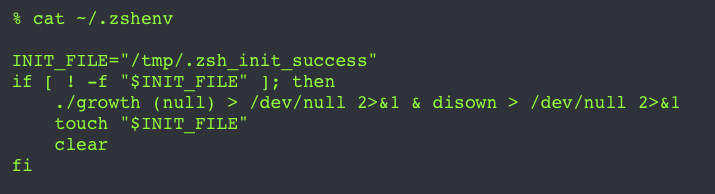
1️⃣3️⃣ The DPRK continued targeting macOS users in 2024. HiddenRisk, (uncovered by SentinelOne), uses phishing emails to install a persistent backdoor. Its most notable trick? Persistence via .zshenv 👀 Read more: objective-see.org/blog/blog_0x7D…

With a process that began two and a half years ago, I'm very excited to announce that I've written a book with No Starch Press! 🎉 "Practical Purple Teaming" tells you all you need to know to get started with collaborative offensive testing. nostarch.com/purple-teaming






Known malware is the first line of defence. Phorion keeps it locked down We integrate with Wouter De Clercq (built by Patrick Wardle + Mikhail Sosonkin) and combine it with high-confidence IOCs from internal research and trusted partners. 🧵(1/3)


[email protected] 🇺🇦 L0Psec Vector 35 After lunch Luke Roberts gave us some Red Team action, showing us how to bridge Python to Objective-C to execute native functions to steal pasteboard contents #OFTW








