Edo Maland
@screetsec
ꜱᴇɴɪᴏʀ ꜱᴇᴄᴜʀɪᴛʏ ᴄᴏɴꜱᴜʟᴛᴀɴᴛ / ᴘᴇɴᴇᴛʀᴀᴛɪᴏɴ ᴛᴇꜱᴛᴇʀ | ᴏꜱᴇᴘ | ᴏꜱᴄᴘ | ᴏꜱwᴘ | ᴏꜱwᴇ | ᴄʀᴛ | ᴄʀᴛᴘ | ᴄʀᴛᴇ | ᴄʀᴛᴏ | ᴇᴡᴘᴛxᴠ2 | ᴇᴄᴛᴘxᴠ2 - ᴡᴀɴɴᴀʙᴇ ʀᴇᴅ ᴛᴇᴀᴍᴇʀ
ID: 1216699056241594369
13-01-2020 12:30:41
89 Tweet
793 Followers
544 Following

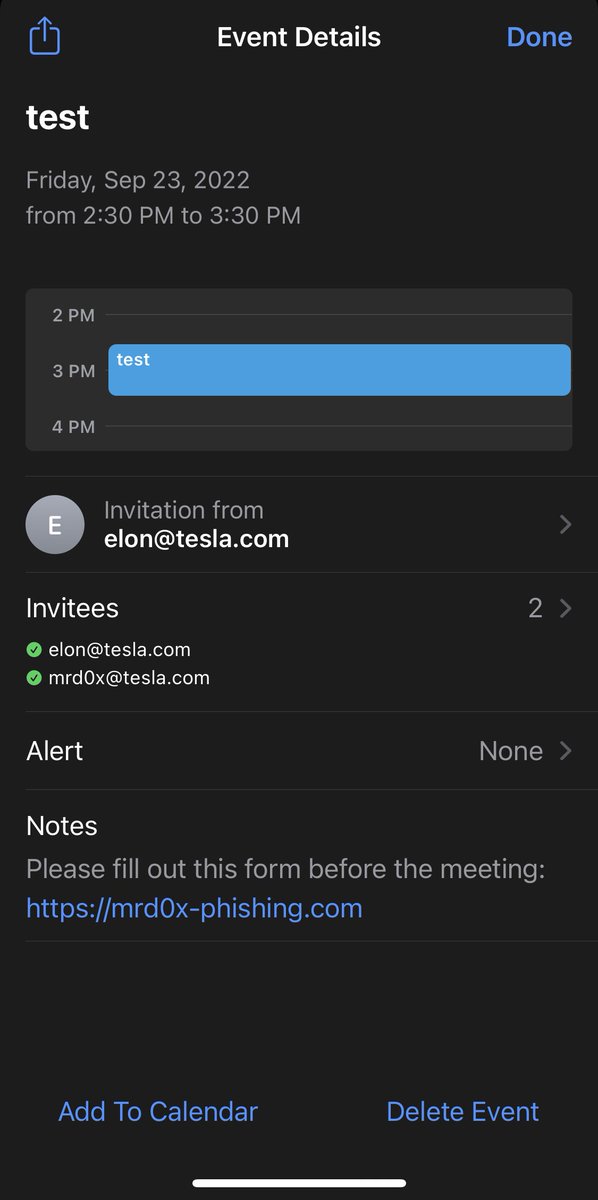
I'm proud to release my recon suites review. Again, thanks to all the developers who make it easy for all hackers and researchers. This time thanks to Harsh Bothra Kathan Patel @eslam3kll Edo Maland j3ssie (Ai Ho) thewhiteh4t Yogesh Ojha 🚀 Piyush Kumar 1/2 six2dez.gitbook.io/pentest-book/o…




















![B:\a.zza (@mcbazza) on Twitter photo Red-Teamers:
[lazy]People like me use Notepad++ as a note-taking thing. We create a 'new', then never get around to saving them.
They get cached here:
C:\Users\{username}\AppData\Roaming\Notepad++\backup
If you hit a dev/sysadmin, you'll find all kinds of crazy stuff. Red-Teamers:
[lazy]People like me use Notepad++ as a note-taking thing. We create a 'new', then never get around to saving them.
They get cached here:
C:\Users\{username}\AppData\Roaming\Notepad++\backup
If you hit a dev/sysadmin, you'll find all kinds of crazy stuff.](https://pbs.twimg.com/media/FDbIXuMXEAAfmBr.png)