stoerchl
@stoerchl
Malware Analyst @HPSecurity | cycling enthusiast and blue jays fan!
ID: 831061763462463488
https://threatresearch.ext.hp.com/blog/?author-filter=46 13-02-2017 08:45:39
379 Tweet
1,1K Followers
102 Following









We published an article about the Magniber ransomware. The malware runs mostly fileless and consistently only uses direct system calls. I find it quite interesting that a ransomware targeting home users has implemented such techniques to bypass detection. threatresearch.ext.hp.com/magniber-ranso…


CaliDog Security's certstream is a great service to monitor new certificates. Unfortunately the service is offline since yesterday. If you decide to run your own certstream-server have a look my pull request as Google took one of the used URLs offline. github.com/CaliDog/certst…




TICKETS, SAVE THE DATE: we will have two batches of ticket sales for #BSidesZH opening soon - Wednesday, July 12th 15:00 (UTC+2/CEST) - Thursday, August 3rd 16:00 (UTC+2/CEST) Price as usual, 10CHF #PleaseRT #InfoSec #DFIR #ThreatIntel Cc Security BSides bsideszh.ch/registration/

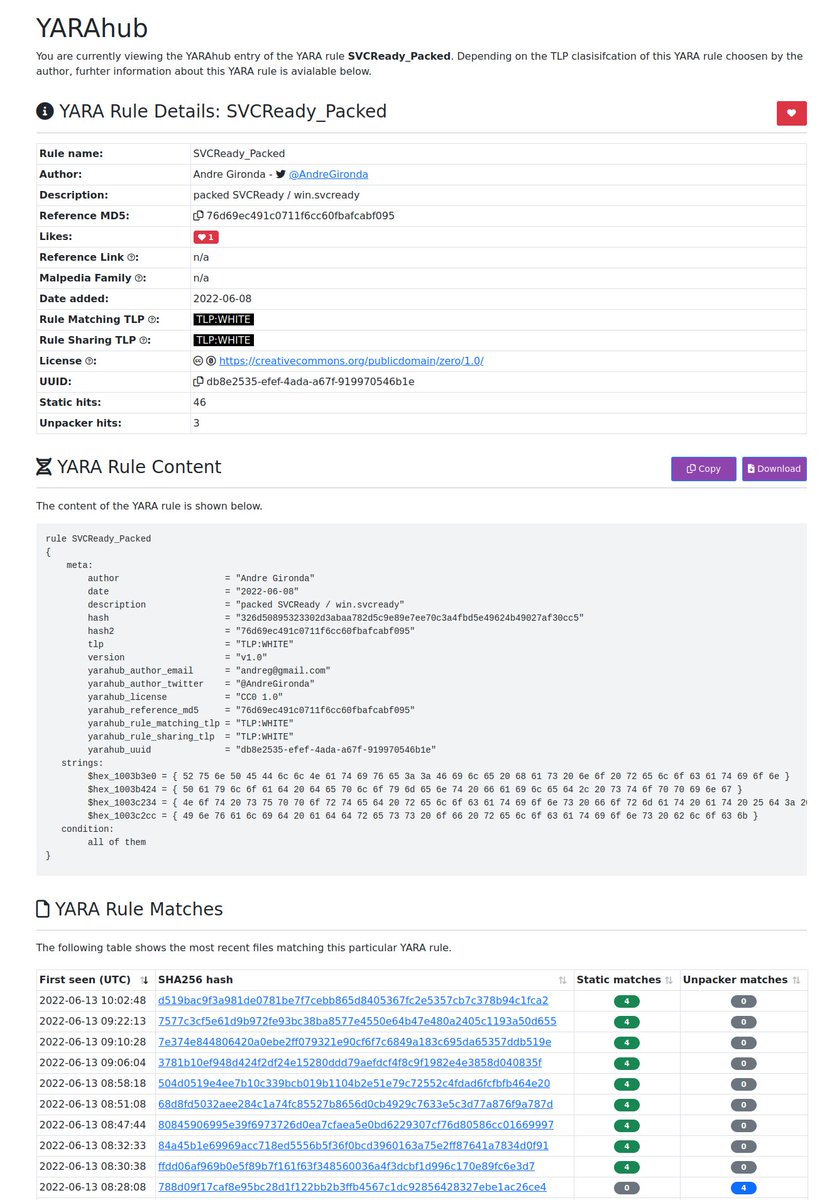
![stoerchl (@stoerchl) on Twitter photo The latest #cutwail campaigs were using payload domains registered on 30 June. In this registration batch, I found three different domains. Two of them were already used in the last two weeks. Therefore I'd guess the next one is:
- dokpio[.]com The latest #cutwail campaigs were using payload domains registered on 30 June. In this registration batch, I found three different domains. Two of them were already used in the last two weeks. Therefore I'd guess the next one is:
- dokpio[.]com](https://pbs.twimg.com/media/FYhCIGyXEAI3T8H.png)
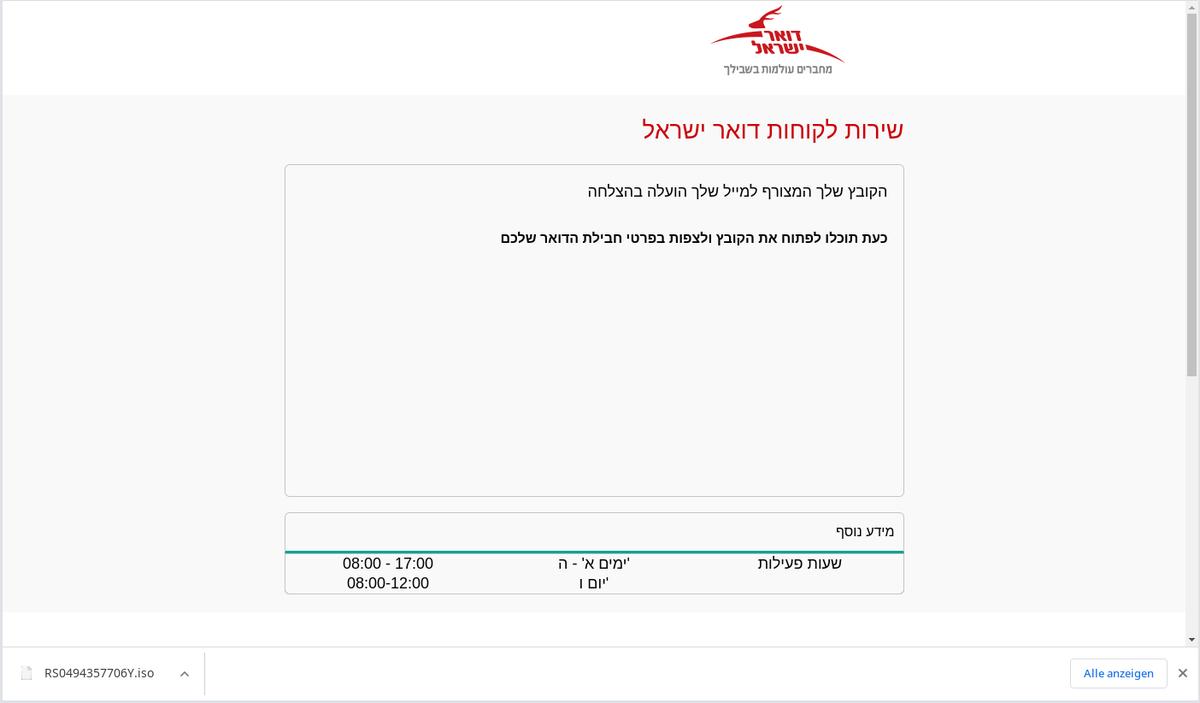
![stoerchl (@stoerchl) on Twitter photo Fake Windows update. Domain registered 3 days ago.
- microsoft-security-updates[.]com
Downloads password protected ZIP file "Windows.zip" (8d93256c7383542996d533cfa1de4696) containing the executable "Windows Update.exe". Unfortunately don't know the password. Fake Windows update. Domain registered 3 days ago.
- microsoft-security-updates[.]com
Downloads password protected ZIP file "Windows.zip" (8d93256c7383542996d533cfa1de4696) containing the executable "Windows Update.exe". Unfortunately don't know the password.](https://pbs.twimg.com/media/FcMz-6eXEAA4ATx.png)
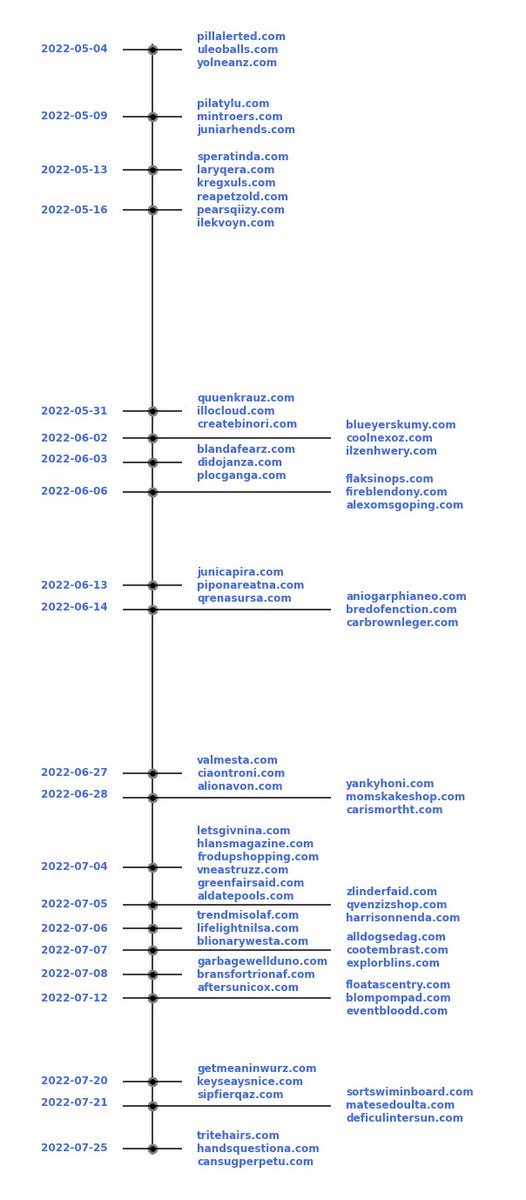
![ThreatDown (@threat_down) on Twitter photo ℹ️ Following the great research by <a href="/stoerchl/">stoerchl</a>, here's a live #Magniber ransomware infection
Magnigate:
goscale[.]uno
Magniber download:
sopush[.]email
In this case the payload was an MSI:
SYSTEM.Antivirus.Hotfix.a6a905ec1f8a.msi
virustotal.com/gui/file/34d40… ℹ️ Following the great research by <a href="/stoerchl/">stoerchl</a>, here's a live #Magniber ransomware infection
Magnigate:
goscale[.]uno
Magniber download:
sopush[.]email
In this case the payload was an MSI:
SYSTEM.Antivirus.Hotfix.a6a905ec1f8a.msi
virustotal.com/gui/file/34d40…](https://pbs.twimg.com/media/FfTwqVQaAAAClZz.jpg)