Sublime Security
@sublime_sec
Sublime Security is the adaptive, AI-powered cloud email security platform that combines best-in-class effectiveness with unprecedented visibility and control.
ID: 1008489013295091718
https://sublime.security 17-06-2018 23:18:12
315 Tweet
2,2K Followers
21 Following






Big thank you to TechAnnouncer for including Sublime in their list of 5 cybersecurity startups “blowing up right now.” We’re rethinking how defenders detect and respond to email threats—with a modular platform built for openness, customization, and control. Read more:







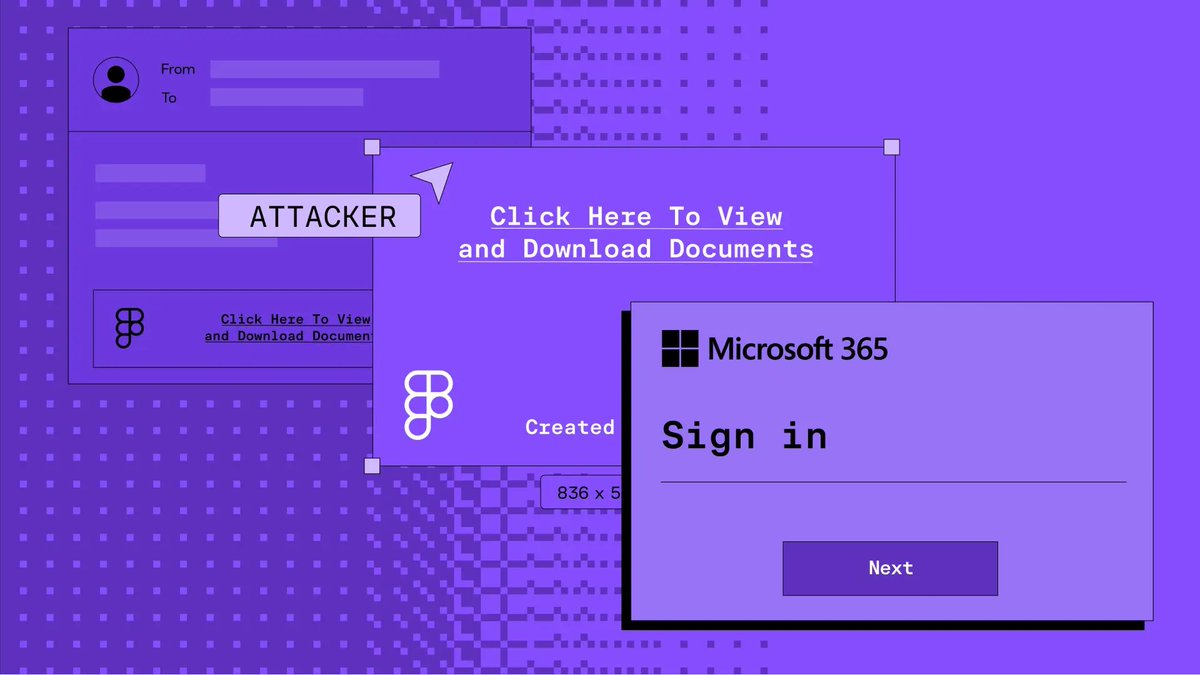

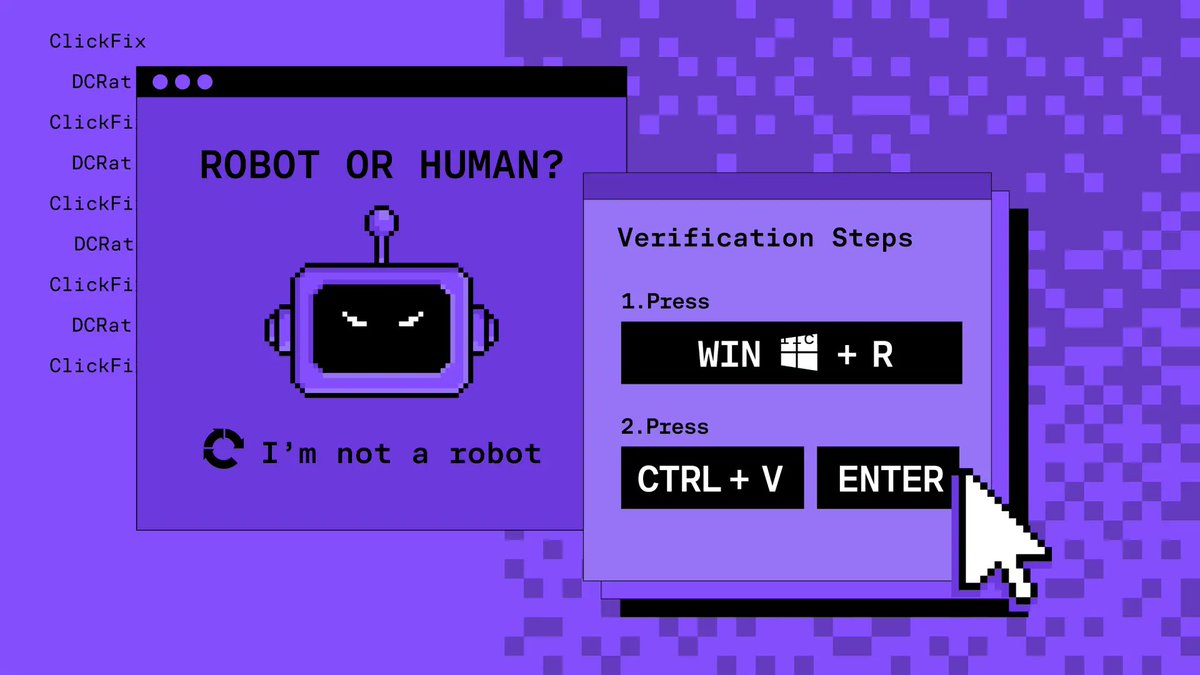

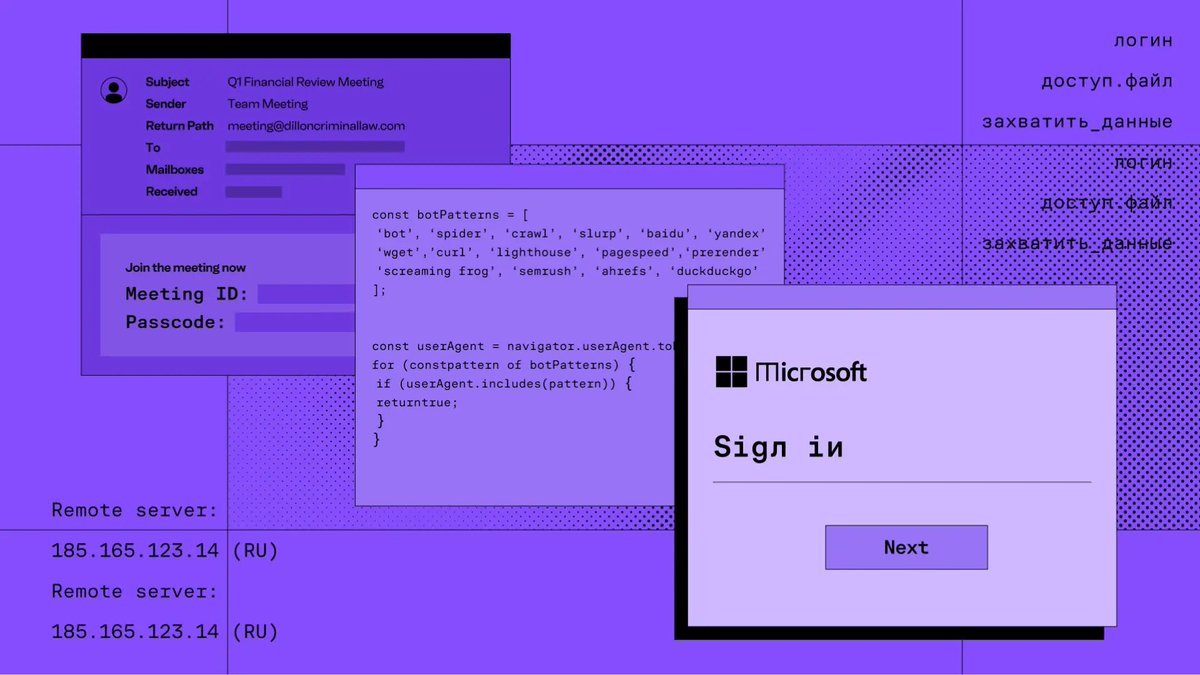
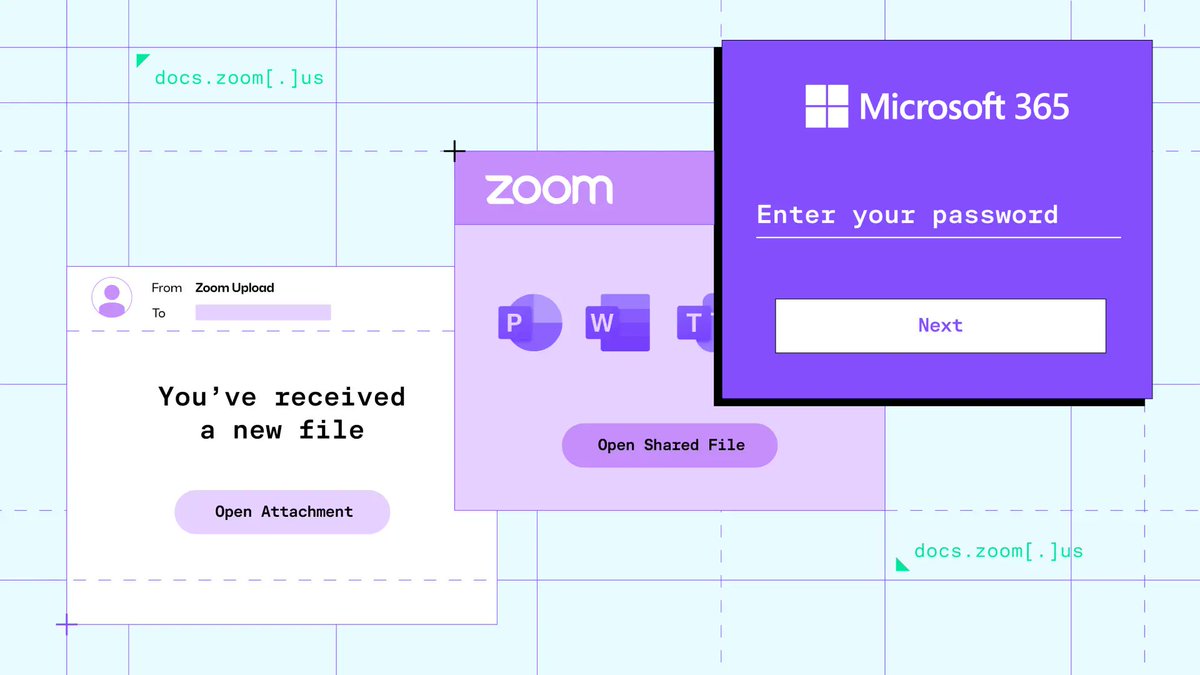
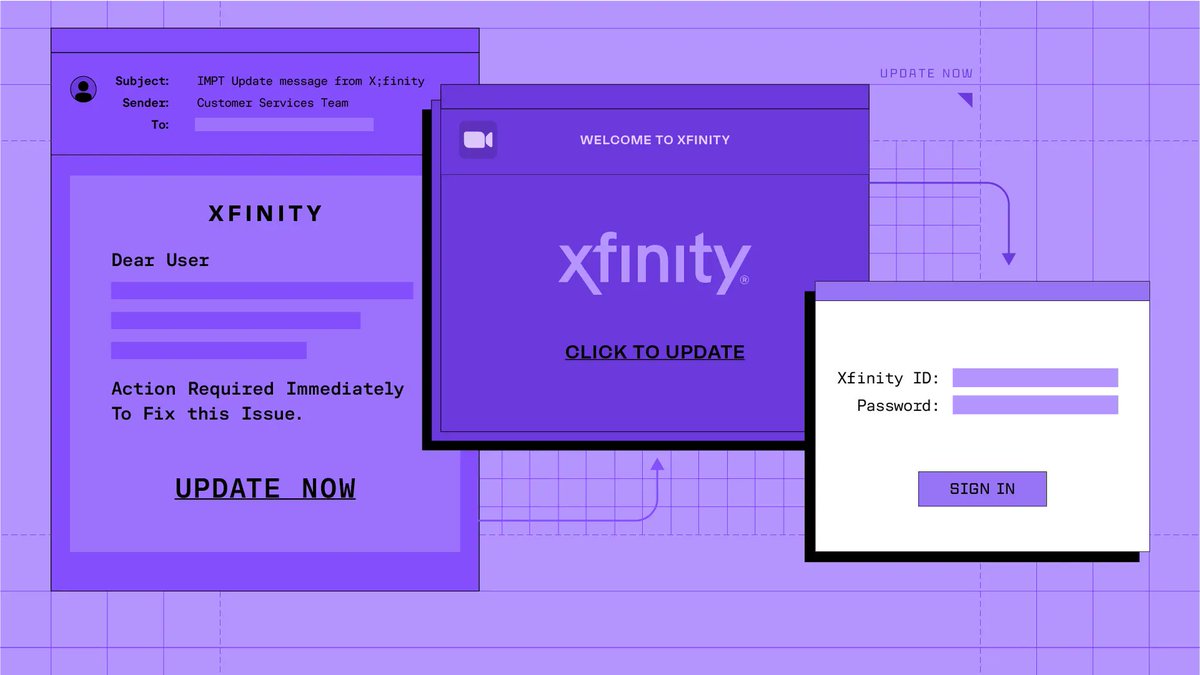
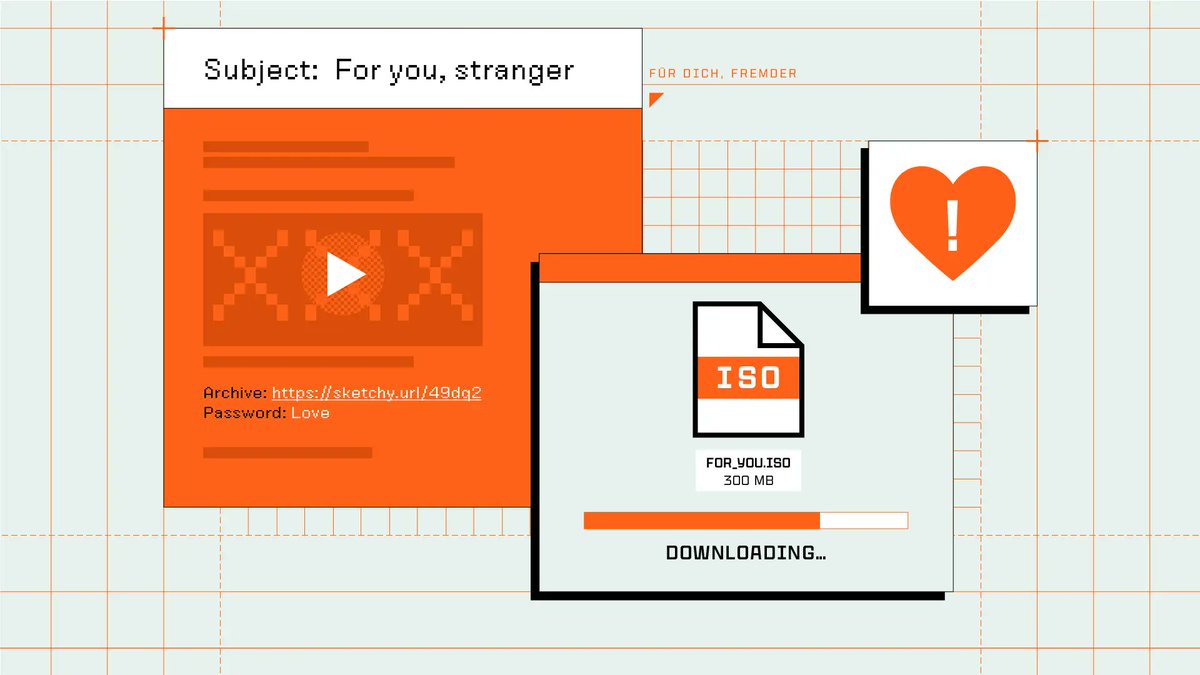
![Sublime Security (@sublime_sec) on Twitter photo In Q1 2025, our research data showed X (formerly Twitter) to be the third-most abused service for email attacks. Learn about a recent credential phishing attack in which a bad actor used the X link shortener (t[.]co) to try to hide a malicious URL: sublime.security/blog/using-the… In Q1 2025, our research data showed X (formerly Twitter) to be the third-most abused service for email attacks. Learn about a recent credential phishing attack in which a bad actor used the X link shortener (t[.]co) to try to hide a malicious URL: sublime.security/blog/using-the…](https://pbs.twimg.com/media/GuTewaUW8AAOLXd.jpg)