terjanq
@terjanq
security enthusiast that loves hunting for bugs in the wild. co-founder and player of @justCatTheFish.
infosec at @google. opinions are mine.
ID: 1090682326709952512
https://github.com/terjanq 30-01-2019 18:45:05
1,1K Tweet
9,9K Followers
239 Following









bugzilla.mozilla.org/show_bug.cgi?i… This is a big change for DOM Clobberers. Firefox Nightly no longer allows native document properties to be overwritten by elements with a name attr, e.g.: <img src=a name=currentScript> <script> alert(document.currentScript)// HTMLScriptElement </script>

For this year Google CTF I created yet another Postviewer challenge called Postviewer v5². The challenge featured a seemingly impossible race-condition. Client-side race-conditions are an under-researched problem and could yield amazing real world bugs! gist.github.com/terjanq/e66c28…

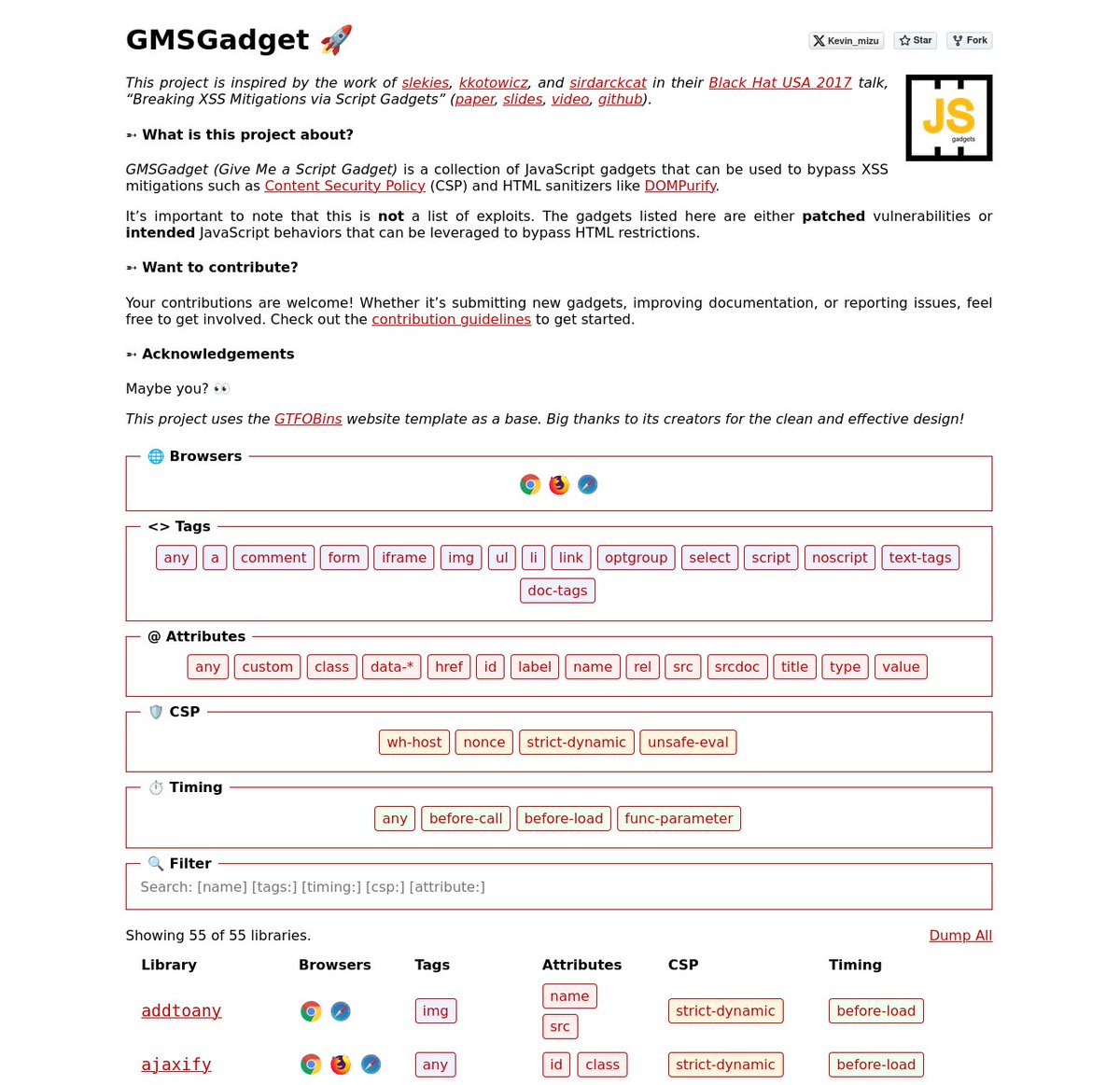
I'm happy to release a script gadgets wiki inspired by the work of Sebastian Lekies, koto, and Eduardo Vela in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4

🎯 JustCTF 2025 - 37h of top-tier online jeopardy CTF action! 🗓️ Starts Aug 2, 0600 UTC 💰 $8,628 prize pool + IDA Pro licenses + swag Big thanks to our sponsors! Trail of Bits OtterSec Hex-Rays SA Zellic 2025.justctf.team | discord.gg/BZqZ7zqC6T #CTF #CyberSecurity



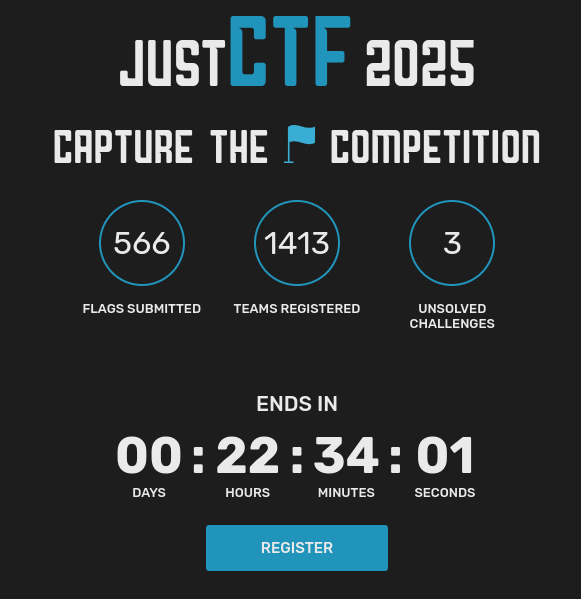
Less than 23 hours to go, and 3 challenges still unsolved! Check 2025.justctf.team Shout-out to our sponsors! Trail of Bits OtterSec Hex-Rays SA Zellic


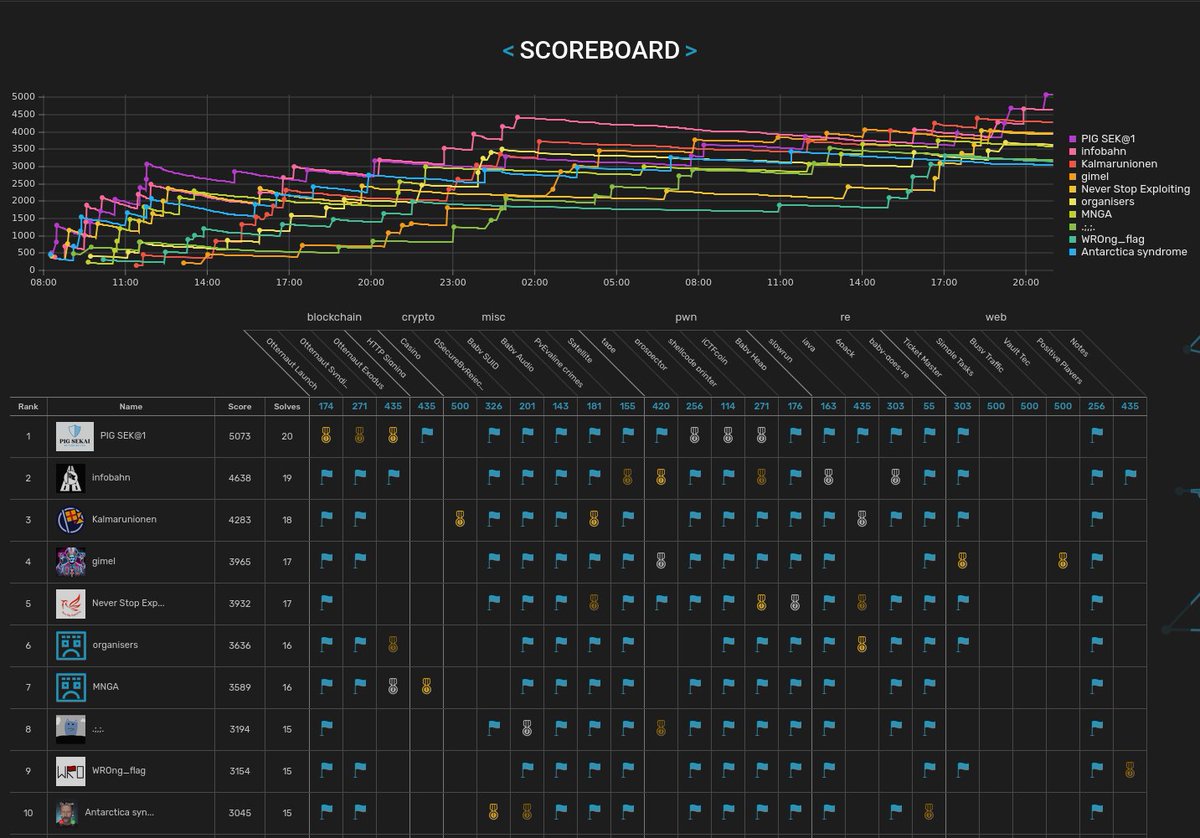
The 2025 edition of the CTF is over! Thanks everyone for playing. Congrats to the first three places: #1 r3kapig + Project Sekai CTF #2 Infobahn #3 Kalmarunionen And also big thanks to our sponsors Trail of Bits OtterSec Hex-Rays SA Zellic