Striker satya2
@tines_io
Security Researcher | Bug Hunter | Microsoft HOF
ID: 1285238600150380545
20-07-2020 15:42:55
710 Tweet
65 Followers
383 Following

Here's a list of bug bounty tools that Godfather Orwa 🇯🇴 uses and shared in Ben Sadeghipour 's live stream. 🧵👇 #bugbounty #bugbountytips







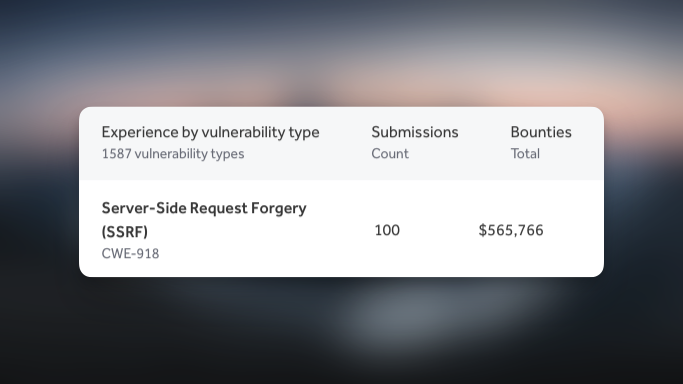
Top Microsoft IIS Thread 🧵:👇 Here is how to find IIS bugs 1) Collect a huge number of targets, subdomains, and ports and even brutforceing the targets 2) Short the IIS services nuclei-templates/fuzzing/iis-shortname.yaml #BugBounty #bugbountytips #infosec Godfather Orwa 🇯🇴





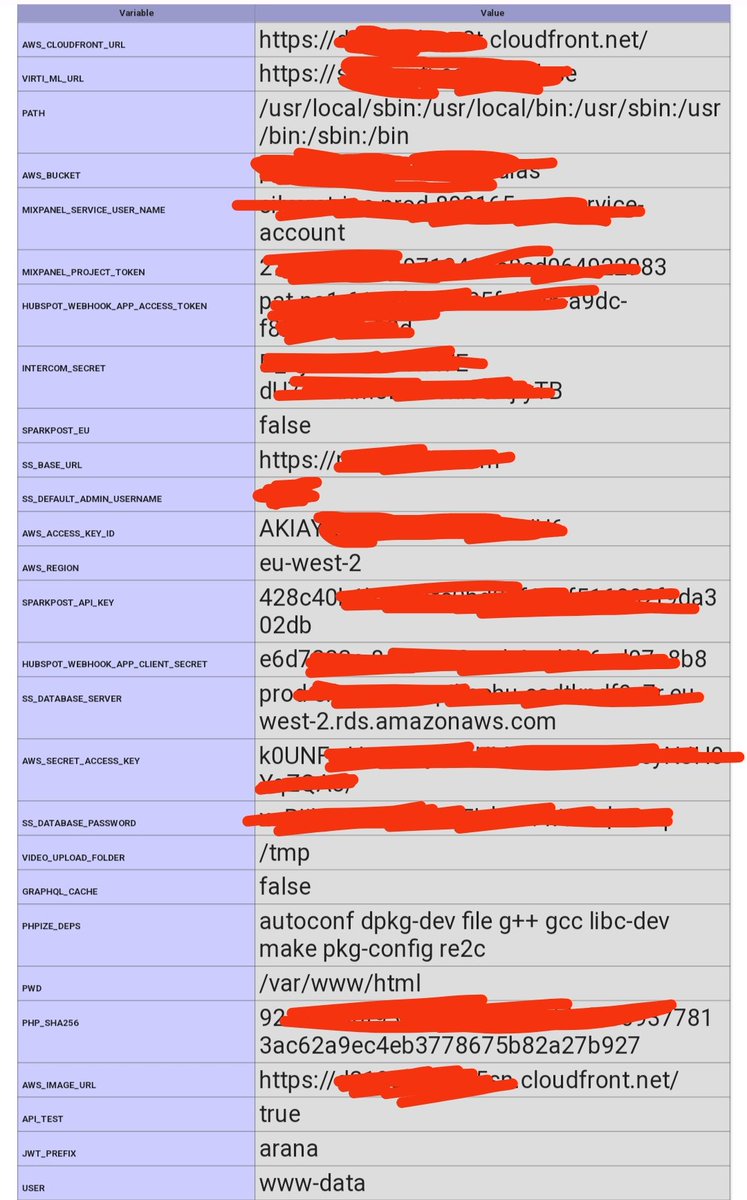
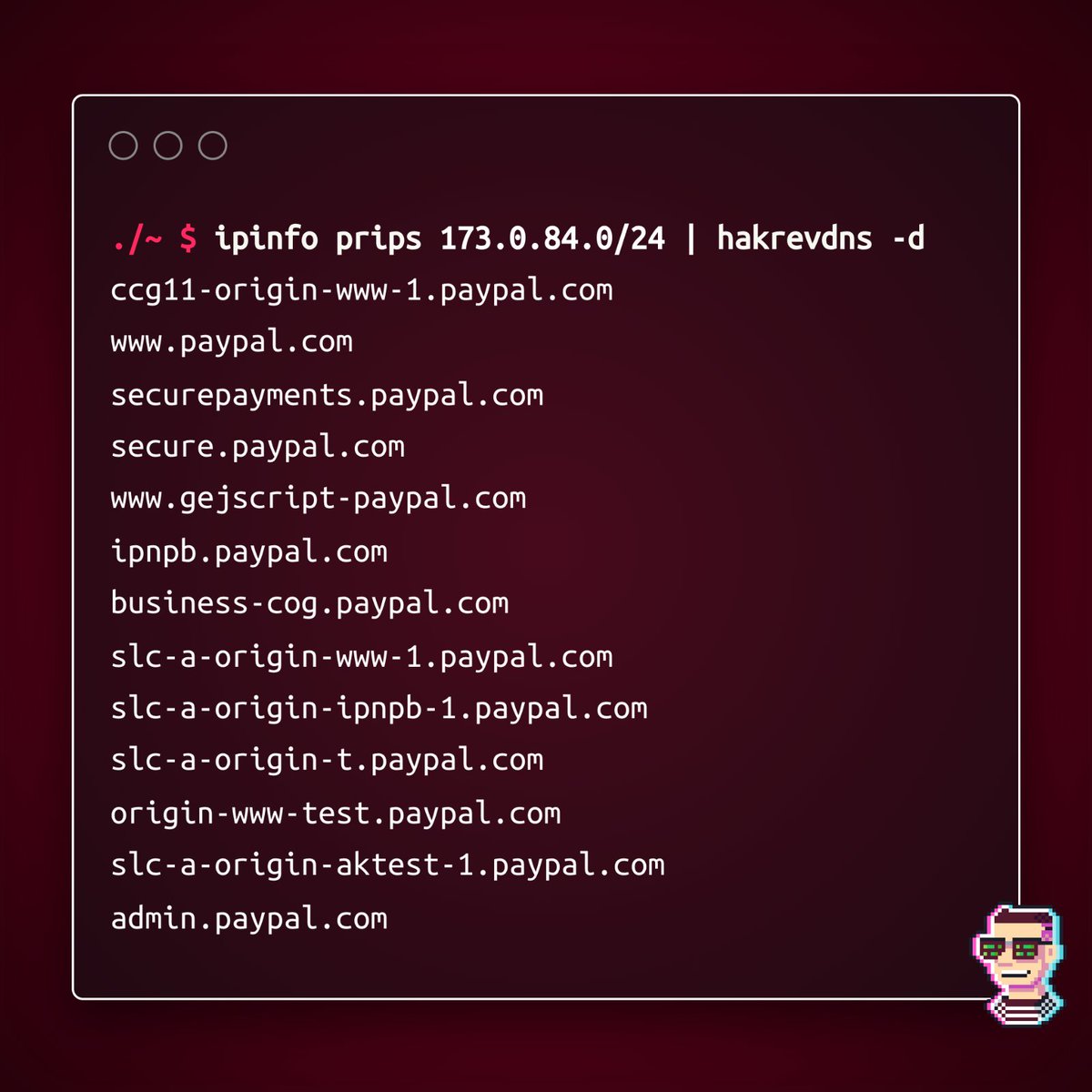
Fuzzing lists - Part 2 Wordlists for few specific Funtions you can use for Specific Purpuses. 1. WEB-INF github.com/orwagodfather/… 2. git_config github.com/random-robbie/… 3. Kubernates / k8s github.com/manojdeshmukh4… 4. log github.com/random-robbie/… 5. pl github.com/orwagodfather/… 6.



Slides of my talk in Security BSides Ahmedabad I hope you like it and found it a little bit useful docs.google.com/presentation/d… #bugbounty #bugbountytip #bugbountytips #infosec Thanks for support for all of you and Security BSides Ahmedabad & bugcrowd