
Vitaly Chipounov
@vitalychh
Chief Architect at Cyberhaven, S2E lead developer
ID: 927912784146436103
http://s2e.systems 07-11-2017 14:57:02
72 Tweet
241 Followers
131 Following


[Wednesday Webinar] 50% of manufacturing executives lack confidence in their #dataprotection. Join Arun DeSouza #CISO of Nexteer Automotive as he shares his insights on Top 3 Security Challenges to Manufacturing #insiderthreats ---> bit.ly/3eHKMLt
![Cyberhaven (@cyberhaveninc) on Twitter photo [Wednesday Webinar] 50% of manufacturing executives lack confidence in their #dataprotection. Join
<a href="/arun_desouza/">Arun DeSouza</a> #CISO of Nexteer Automotive as he shares his insights on Top 3 Security Challenges to Manufacturing
#insiderthreats ---> bit.ly/3eHKMLt [Wednesday Webinar] 50% of manufacturing executives lack confidence in their #dataprotection. Join
<a href="/arun_desouza/">Arun DeSouza</a> #CISO of Nexteer Automotive as he shares his insights on Top 3 Security Challenges to Manufacturing
#insiderthreats ---> bit.ly/3eHKMLt](https://pbs.twimg.com/media/EWnj8zwUYAIWmsa.jpg)










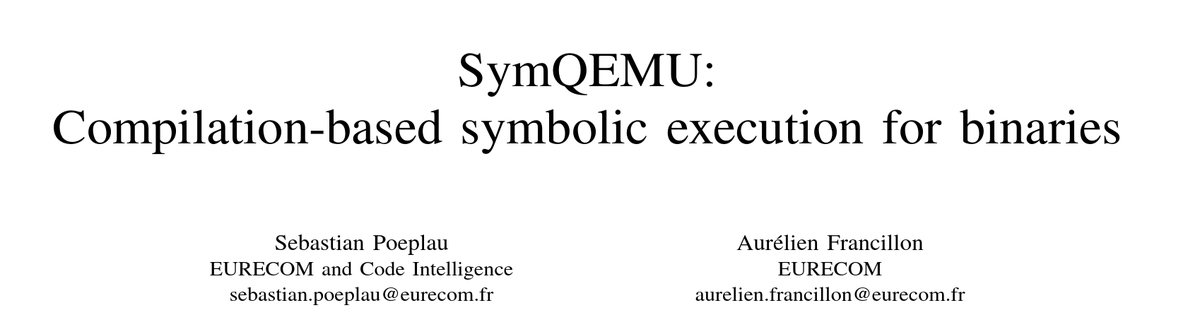
Our new paper (to appear at NDSS 21) with Sebastian Poeplau SymQEMU: Compilation-based symbolic execution for binaries Like for SymCC we directly embed the instrumentation for symbolic execution in the app, but this time in QEMU, so works with binaries PDF: s3.eurecom.fr/docs/ndss21_sy…


Thrilled to announce that our paper "Themis: Ambiguity-Aware Network Intrusion Detection based on Symbolic Model Comparison" got accepted at ACM CCS 2025 #ccs2021 #ccs21. Many thanks to all co-authors and also the reviewers for their feedback! Full paper: bit.ly/3tIw7YB


Thrilled to announce our $33M Series B fundraise and welcome Satish Dharmaraj and @redpointvc, William Lin and Forgepoint Capital, and Jake Flomenberg and Wing VC as new Cyberhaven investors! cyberhaven.com/celebrating-cy…



"The S2E Platform: A Journey from a Research Prototype to a Commercial Product" -- delighted to announce the fourth and final keynote at the upcoming KLEE workshop, from Vitaly Chipounov of Cyberhaven. srg.doc.ic.ac.uk/klee22/keynote…


Having spent 10 years architecting, building & running the engineering team for the world’s leading endpoint security product, it was refreshing to be able to put some thoughts down on paper with the Cyberhaven team, especially with the tens of “agents” on corporate machines.






