
James Wickett
@wickett
CEO & Co-Founder at DryRun Security, Instructor at LinkedIn Learning, and Univ. of Oklahoma Alum. For speaking requests: wickett.me
ID: 14836673
https://dryrun.security 19-05-2008 19:10:29
11,11K Tweet
5,5K Followers
1,1K Following

A talk about DevOps, Security, and AI by James Wickett DevOpsDays Austin #devopsdaysaustin


Thanks Ernest Mueller! Also thanks for the cameo appearance.

Learning about distributed tracing from Josh Lee at #devopsdays DevOpsDays Austin #devopsdaysaustin


The slides from my talk at #devopsdays #devopsdaysaustin DevOpsDays Austin A Talk about DevOps, Security, and AI speakerdeck.com/wickett/a-talk…

The 8 fallacies of distributed computing (circa 1990s) @nicksilkey DevOpsDays Austin #devopsdaysaustin #devops


The 8 Fallacies of a Distributed Organization @nicksilkey #devopsdays DevOpsDays Austin #devopsdaysaustin


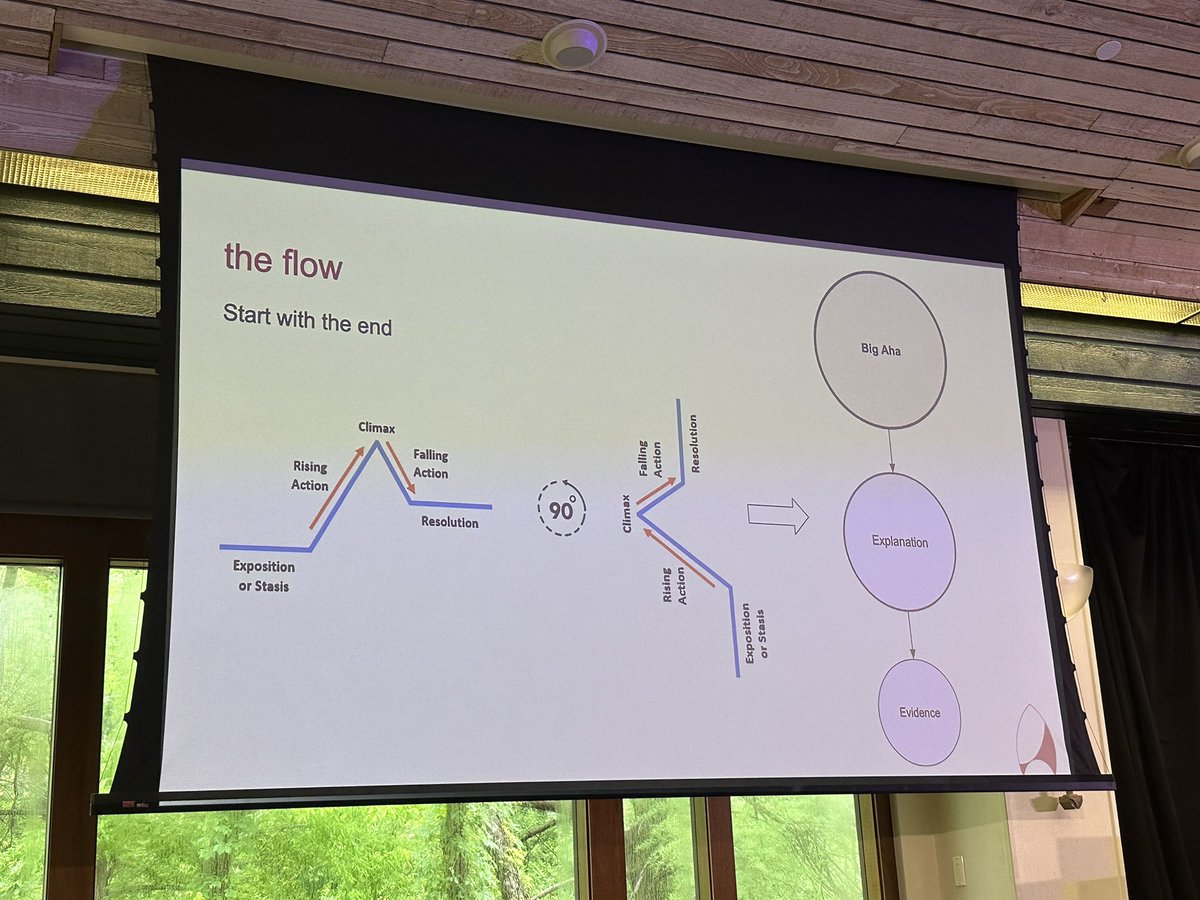
To tell stories with data, consider the 90 degree turn (E pluribus unum) Peco Karayanev DevOpsDays Austin #devopsdaysaustin #devopsdays





🤖 One Year of Using LLMs for Application Security: What We Learned Ken Johnson shares key lessons learned and challenges faced Tips: - Use the right LLM for the task (e.g. some specialize in embeddings, or understanding code) - The value of RAG - Combining deterministic and

We're thrilled to welcome DryRun Security to the LiveOak portfolio! DryRun raised $8.7M in seed funding to transform app security with AI-powered risk detection. Congrats to James Wickett, Ken Johnson & team! #WelcometotheLiveOakPortfolio









