Xin'an Emmanuel Zhou
@zhouxinan
A 🏳️🌈 Computer Security PhD candidate at @UCRiverside.
ID: 3062627454
https://xinanzhou.com/ 05-03-2015 10:14:03
337 Tweet
727 Followers
673 Following

After two years of hard work with Damien Cauquil (@[email protected]) , we are proud to release for DEFCON32 the first public version of WHAD, a whole new ecosystem of opensource libs, tools & firmwares for wireless security ! The main repo is here: github.com/whad-team/whad… . And now, demo time ! [1/n]



Qian, et al Zhiyun Qian from UC Riverside presented at BlackHat blackhat.com/us-24/briefing… about systemic problems with the consumer wifi wireless mesh networks due to broken trust models and security flaws

Happy to share one paper to be presented this week in USENIX Security "That Doesn't Go There: Attacks on Shared State in Multi-User Augmented Reality Applications". Work done with Carter Slocum, Erfan Shayegani , Pedram Zaree, Jiasi Chen, and Nael Abu-Ghazaleh. Talk is on 08/15 at 10:45 am.


Check out Zhai Yizhuo’s talk if you’re at USENIX Security!




Xin'an Emmanuel Zhou will present "Untangling the Knot: Breaking Access Control in Home Wireless Mesh Networks" at ACM CCS 2024 this afternoon at 2:15pm. We show a LAN attacker can gain root shells on access points, affecting popular vendors such as Netgear, Asus, TP-link, Linksys.


I am recruiting PhD students & Postdocs on AI Security, LLM Agents, Code Generation research at UMD Computer Science UMD Department of Computer Science & Maryland Cybersecurity Center Maryland Cybersecurity Center (MC2) For PhD program pls mention me in your application cs.umd.edu/grad/apply. For Postdocs please email me.


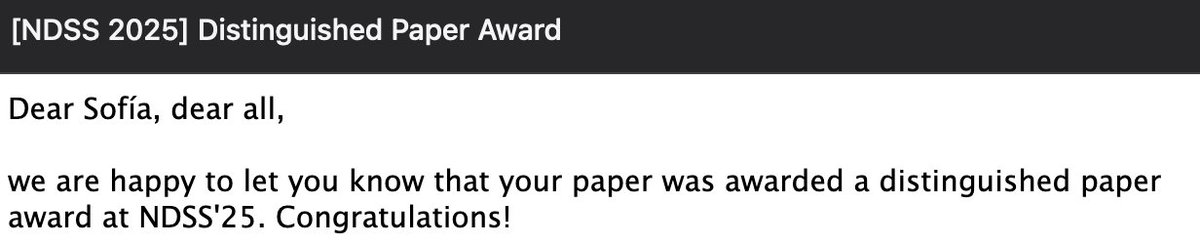
Our beautiful "DiStefano" - a zkTLS protocol- paper (with Hamed alexー gpestana Joe Rowell) just won Distinguished Paper Award at NDSS Symposium ! eprint.iacr.org/2023/1063.pdf Such an honour! Upcoming work as part of Brave coming!!



EntrySign was nominated for two Pwnies (best crypto bug and best desktop bug)! 🥳 youtube.com/live/TuKPA-CeD… spq Eduardo Vela Tavis Ormandy


Untangling the Knot (untanglingthekn0t.com) was nominated for Best Cryptographic Attack at the Pwnie Awards 2025. It uncovers fundamental flaws of crypto protocols in mesh Wi-Fi systems. Exploits and summary: untanglingthekn0t.com