Nick Powers
@zyn3rgy
Adversary Simulation @SpecterOps | Previously @Rapid7 & @Protiviti
ID: 1319352285298917377
https://github.com/zyn3rgy 22-10-2020 18:58:02
264 Tweet
1,1K Followers
220 Following


The talk Nick Powers and I gave at BSides Charleston titled Doe-n’t Play Fair was posted a couple days ago! It was our first dive into game hacking outside of some basic Cheat Engine hacks in middle school. The meme about red team techniques being downstream from game hacking is so real


You can now use LDAP/LDAPs protocols with the SOCKS proxy of ntlmrelayx thanks to the PR from Pierre Milioni (now merged upstream). Here is an example with ldeep using relayed authentication from HTTP to LDAPs :




BIG NEWS: SpecterOps raises $75M Series B to strengthen identity security! Led by @InsightPartners with @AnsaCapital, M12 - Microsoft's Venture Fund, Ballistic Ventures, Decibel, and Cisco Investments. ghst.ly/seriesb #IdentitySecurity #CyberSecurity (1/6)



A reoccurring necessity on assessments, this is a 🔥 resource from Matt Creel



I'm super happy to announce an operationally weaponized version of Yuval Gordon's BadSuccessor in .NET format! With a minimum of "CreateChild" privileges over any OU it allows for automatic escalation to Domain Admin (DA). Enjoy your inline .NET execution! github.com/logangoins/Sha…




Chatting with mah fwend and co-worker Jonny Johnson to learn all about Event Tracing for Windows, and some super cool projects he has been working on: a lightweight and custom "toy EDR" JonMon and ETWInspector to help with Windows telemetry research! youtu.be/BNWAxJFL6uM



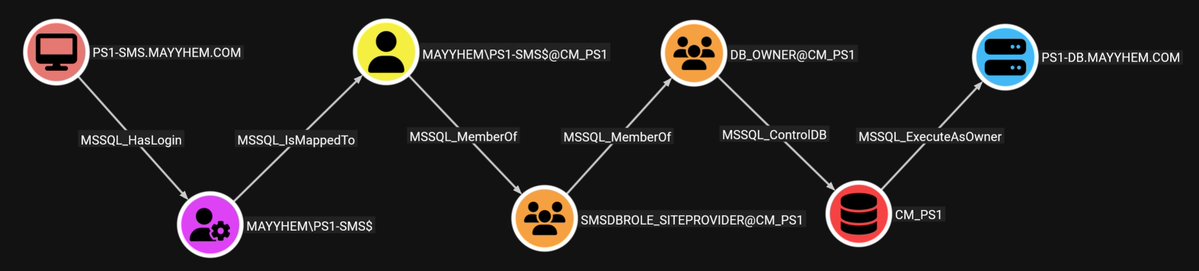
Great walkthrough of an attack path that can be challenging to setup properly over C2. Thanks for the shoutout Melvin langvik !


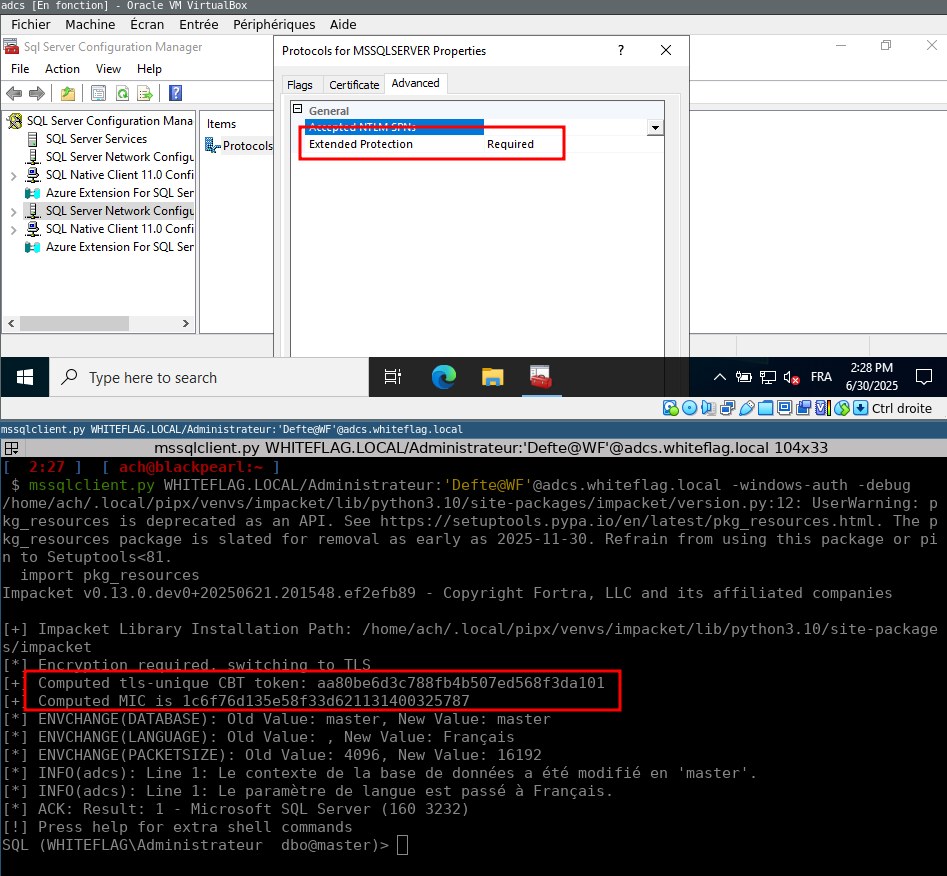
Reverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (Aurélien Chalot), including instructions for reproducing the test environment yourself. (link below)