
SinSinology
@sinsinology
Pwn2Own 20{22,23,24,24.5,25}, i look for 0-Days but i find N-Days & i chase oranges 🍊
ID: 1003519631389331457
https://summoning.team/ 04-06-2018 06:11:39
2,2K Tweet
13,13K Followers
624 Following

(^-^) Don't rush, 4 seats left for "Advanced .NET Exploitation" September edition at RomHack 2025 (Cyber Saiyan | RomHack Conference, Training, Camp) summoning.team




Congrats to Ken Gannon (@yogehi) of NCC Group (NCC Group Research & Technology) for winning the Pwnie for Best Mobile Bug for his #Samsung exploit he used at #Pwn2Own Ireland! We hope he returns in a few weeks with something even better.







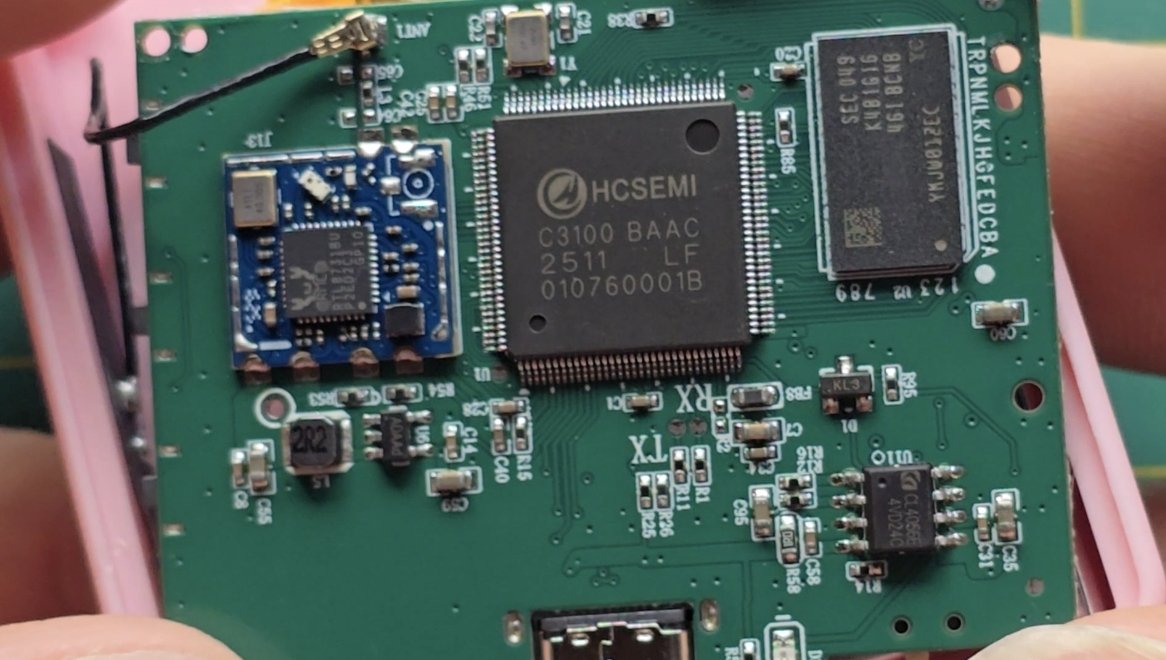
Tomorrow 7 PM PDT! Livestream w me and MalwareTech. We’ll look at this month’s Patch Tuesday, dissect a bindiff, and try to turn it into an exploit. I might also try to get him to solve the STILL UNSOLVED Windows Phrack CTF challenge 🤔 twitch.tv/malwaretechblog












![UFC (@ufc) on Twitter photo #ANDNEW!!
[ #UFC319 | B2YB: <a href="/TerminalListPV/">The Terminal List</a> ] #ANDNEW!!
[ #UFC319 | B2YB: <a href="/TerminalListPV/">The Terminal List</a> ]](https://pbs.twimg.com/media/Gyh3HdTaIAAtd10.jpg)