
Ruben V Piña
@ruben_v_pina





I hope everyone got some rest after DownUnderCTF this weekend. My colleague hashkitten wrote up a blog post on a novel technique for SQL Injection in PDO's prepared statements, required to exploit the “legendary” challenge, which only got one solve: slcyber.io/assetnote-secu…

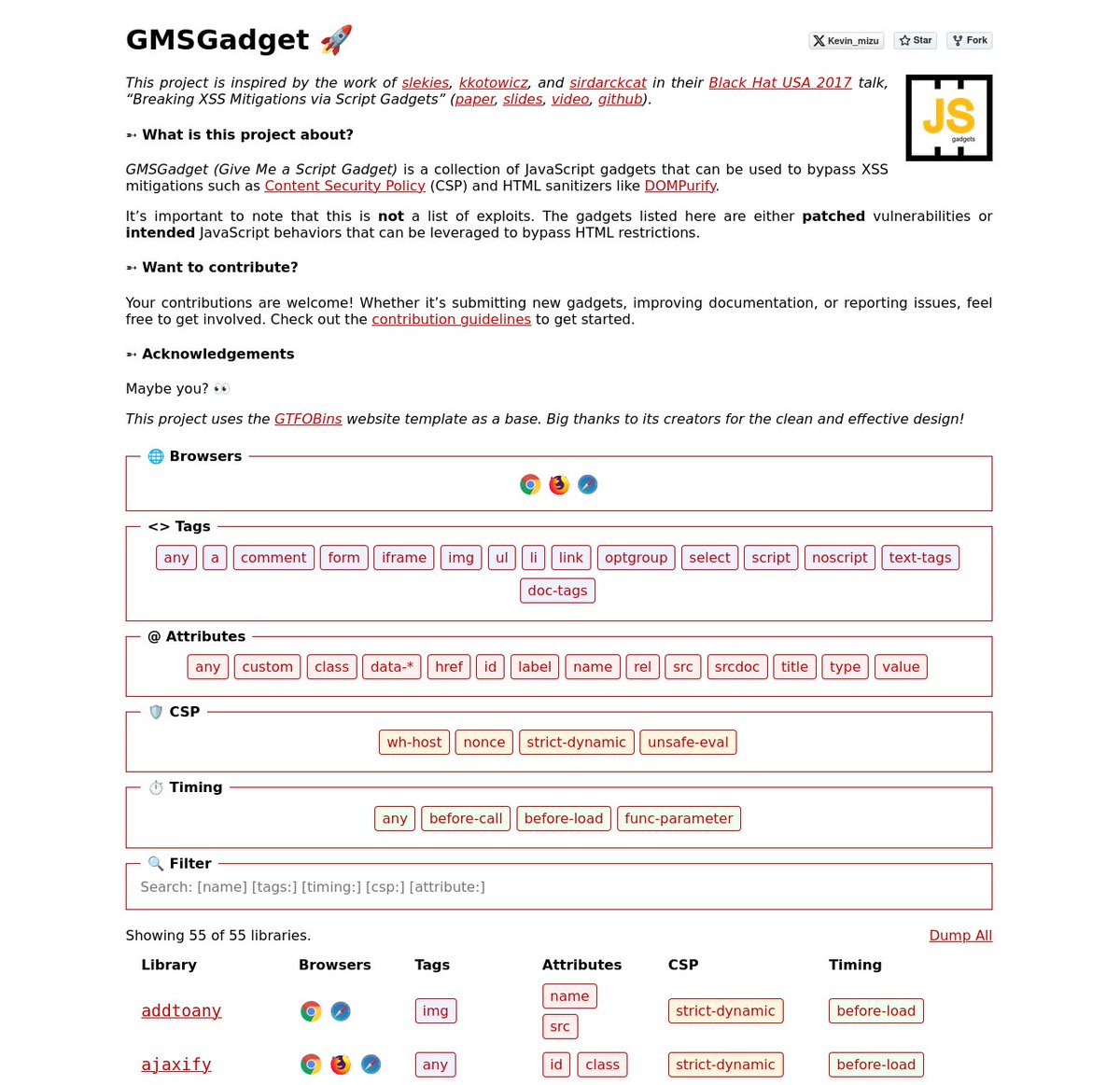
I'm happy to release a script gadgets wiki inspired by the work of Sebastian Lekies, koto, and Eduardo Vela in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4


🚨New Black Hat research released: Over $200k in bounties earned in just two weeks. Join the movement to kill HTTP/1.1 today ⬇️ 🔍PortSwigger’s James Kettle (James Kettle) introduces two new classes of HTTP desync attacks capable of compromising credentials on tens of millions of


🚨New Black Hat research released: Over $200k in bounties earned in just two weeks. Join the movement to kill HTTP/1.1 today ⬇️ 🔍PortSwigger’s James Kettle (James Kettle) introduces two new classes of HTTP desync attacks capable of compromising credentials on tens of millions of



ActiveScan++ can now detect multiple advanced unicode exploits just dropped at #BHUSA including confusables, codepoint overflows, case-conversion and combining diacritics! Thanks to researchers Ryan Barnett (B0N3) @ hackersummercamp & Angel Hacker for contributing this awesome update.





Moving to upstream HTTP/2 slams the door on desync attacks. Binary framing eliminates the ambiguity HTTP/1.1 suffers from, reducing exploitability. In this blog, James Kettle, Director of Research at PortSwigger, outlines a clear case for replacing HTTP/1.1 with HTTP/2 to prevent


Thanks PortSwigger and Bug Bounty Village for this awesome event — and also to my DEVCORE buddies for standing on stage to collect the trophy for me! A little follow-up article on this research is coming soon... stay tuned! 🤘


Orange Tsai 🍊 Ariel Garcia PortSwigger Bug Bounty Village DEVCORE Congrats, that research was top tier! I got one too 🙏




How they hacked 24 million websites... by accident! 😮 A simple investigation into a redirect bug turned into one of the largest accidental website compromises James Kettle has ever seen. Security researcher groeneappel ⵣ found an H2.0 desync on a Heroku-hosted site behind




